[AWS SAA-C02 Study Note] Security: VPC, IAM, NACLs, WAF
VPC
Virtual Private Cloud
provision a logically isolated section of AWS cloud where you can launch AWS resources in a virtual network that you define
Core Components
think AWS VPS as your own personal data center
gives you complete cointrol over your virtual networking environment
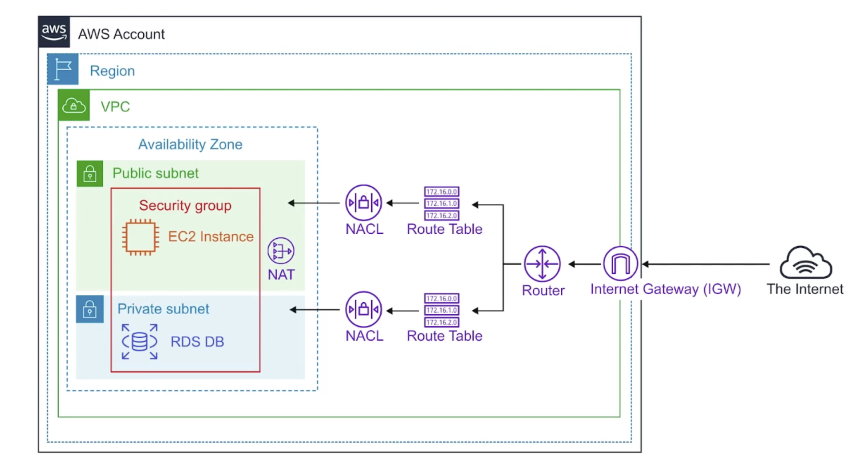
- Internet Gateway (IGW)
- VPN Gateway
- Routing Tables
- Network Access Control Lists (NACLs) - Sateless
- Security Group (SG) Stateful
- Public Subnets
- Private Subnets
- Nat Gateway
- Customer Gateway
- VPC Endpoints
- VPC Peering
Key Features
Default VPC
0.0.0.0/0
it represents all possible IP address
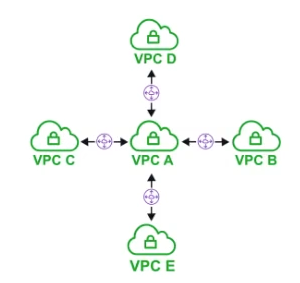
VPC Peering
allows you to connect one VPC with another over a direct network route using private IP address
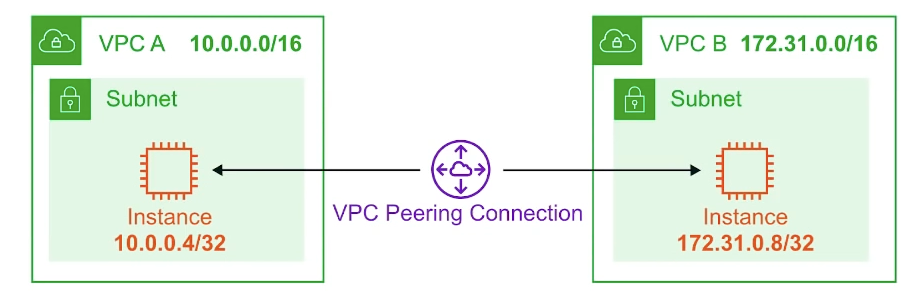
instance on peered VPCs behave just like they are on the same network
connect VPCs across sma e or different AWS account and regions
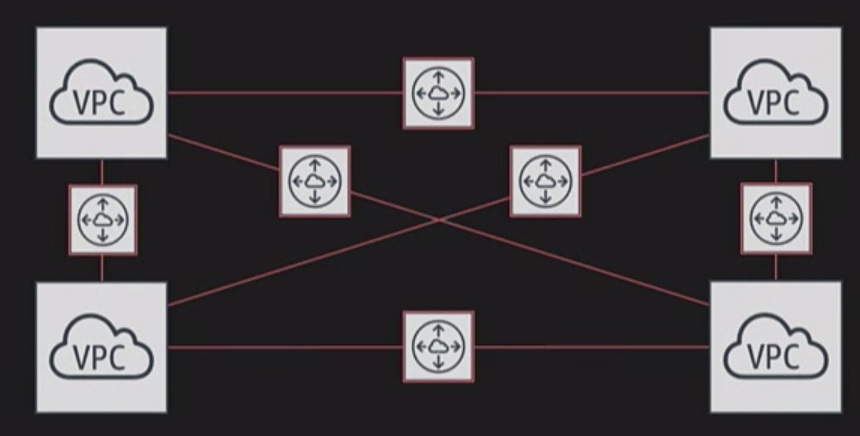
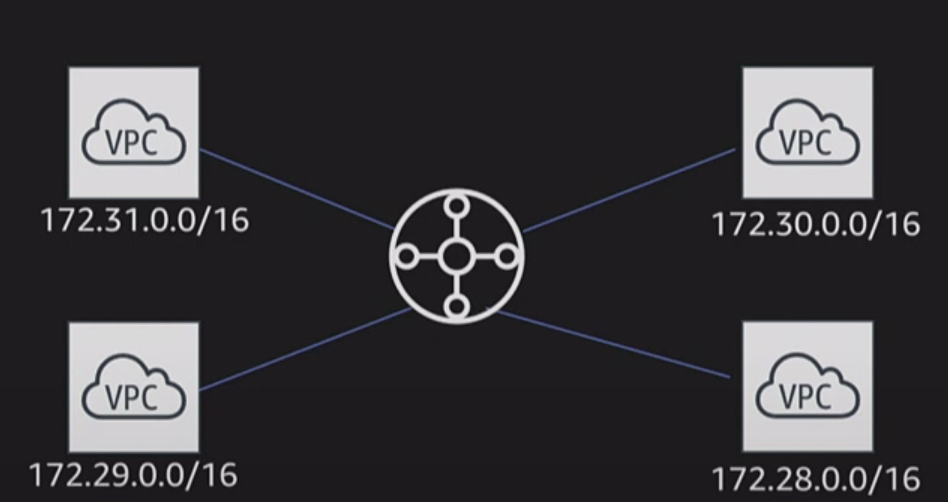
peering uses Star Configuration: 1 central VPC - 4 other VPCs
no transitive peering (peer must take place directly between VPCs)
needs a one to one connect to immediate VPC
No Overlapping CIDR (Classless Inter-Domain Routing、CIDR) Blocks
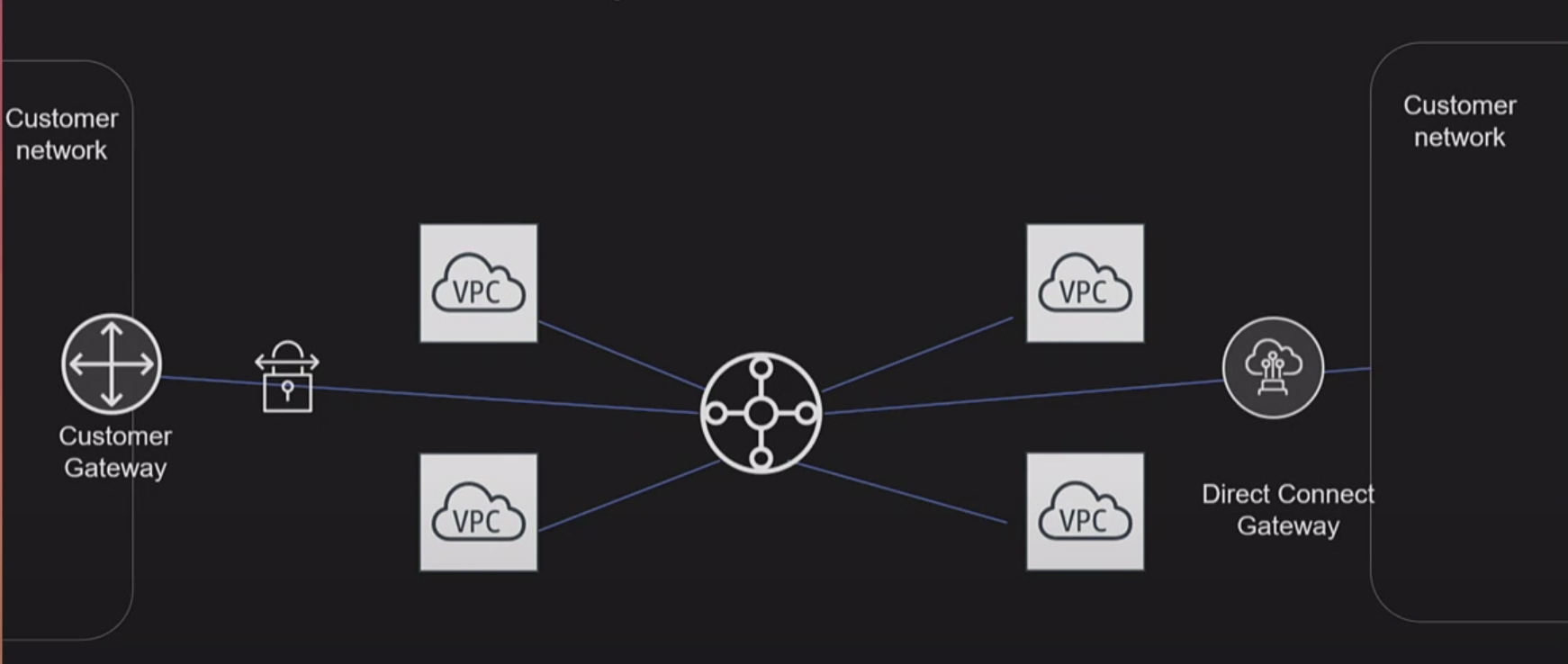
Transit Gateway (TGW)
somehow a upgrade version of AWS Direct Connect and VPC Peering
!!!To deal with inter-VPC connection in more complex situation!!!
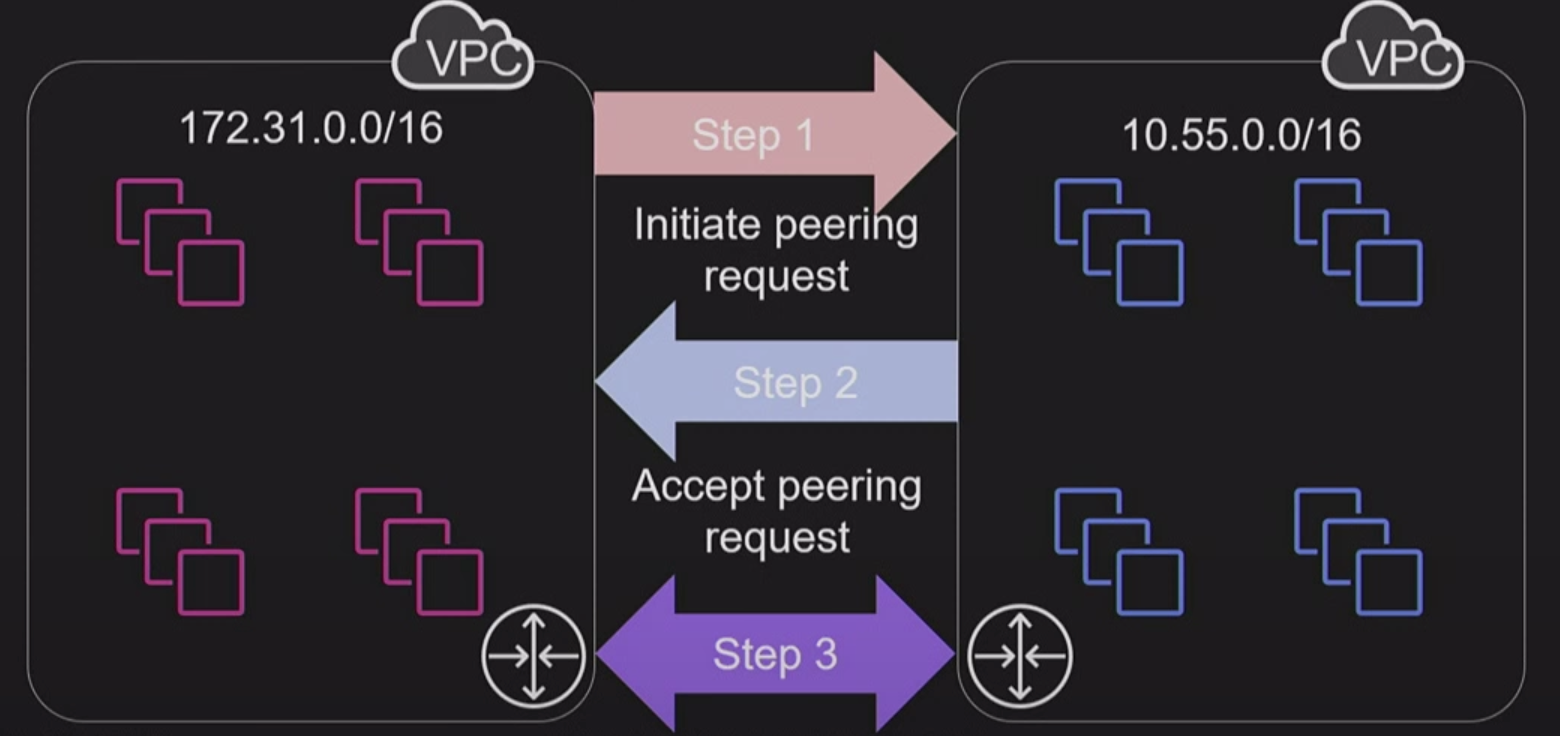
Process of Extablishing a VPC Peering
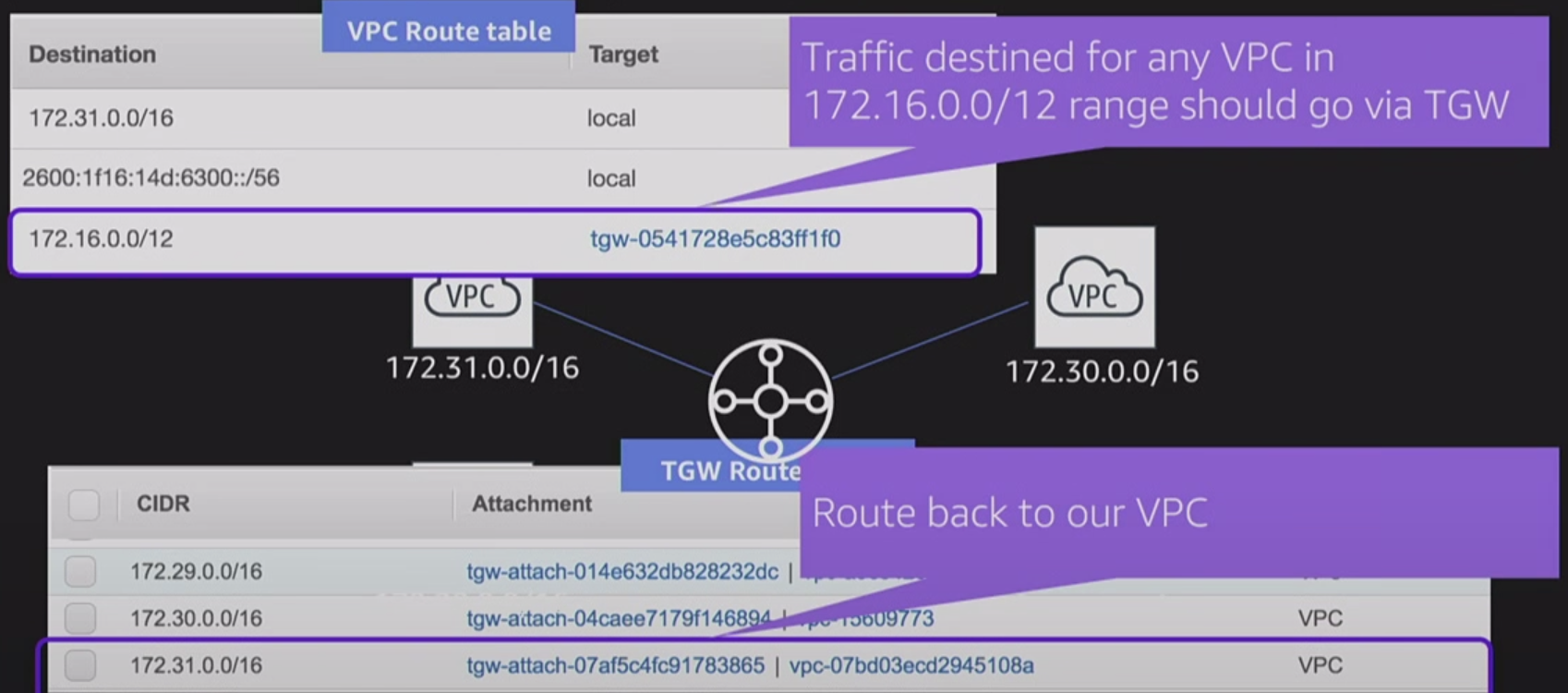
Route Tables
- route table are used to determine where network traffic is directed
- each subnet in your VPC must be associated with a route table
- a subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same route table
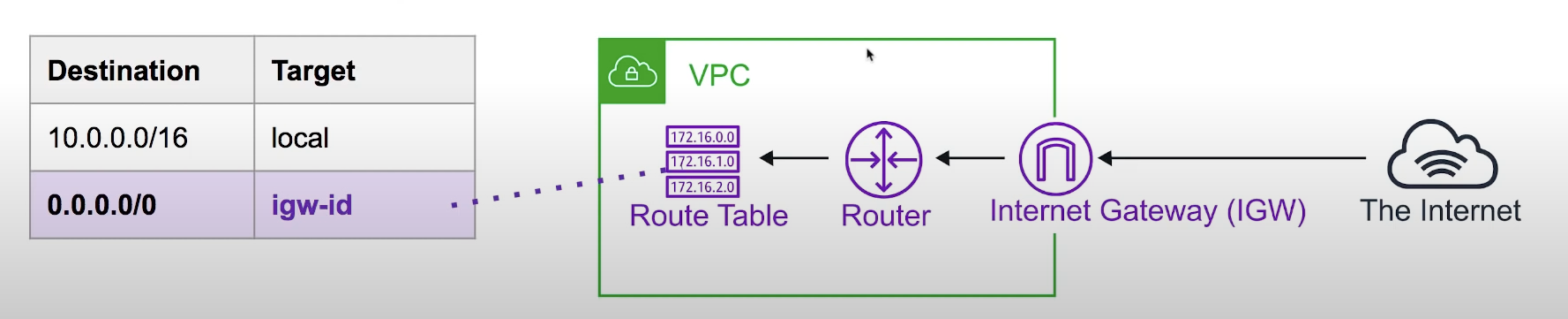
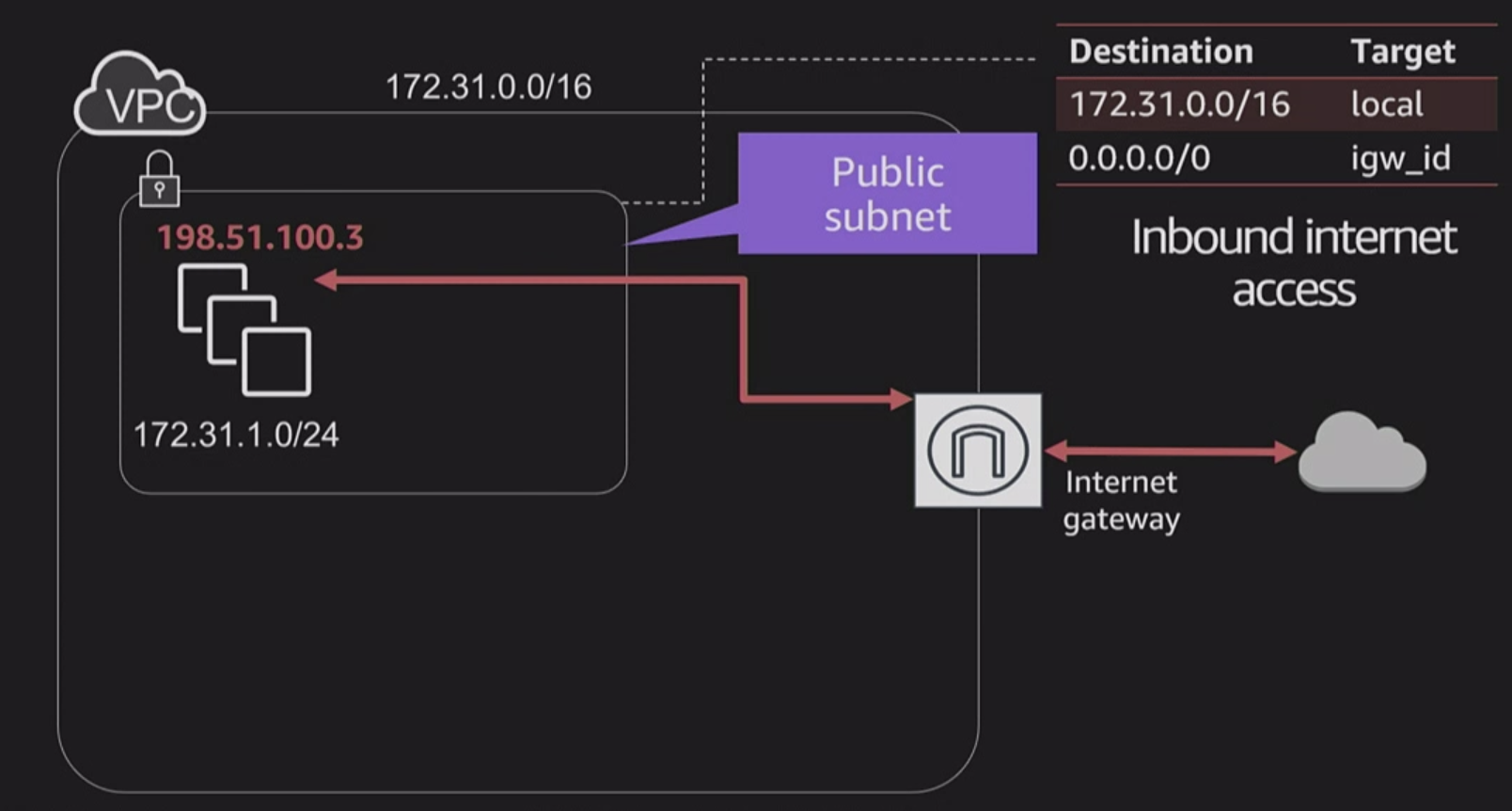
IGW
IGW allows your VPC access to Internet
- provide a target in your VPC route tables for internet-routable traffic
- perform network access address translation (NAT) for instances that you have been assigned public IPv4 addresses
Bastion/Jumpbox
Bastion are EC2 instances which are security harden. They are designed to help you gain access to your EC2 instances via SSH or RCP that are in a private subnet.
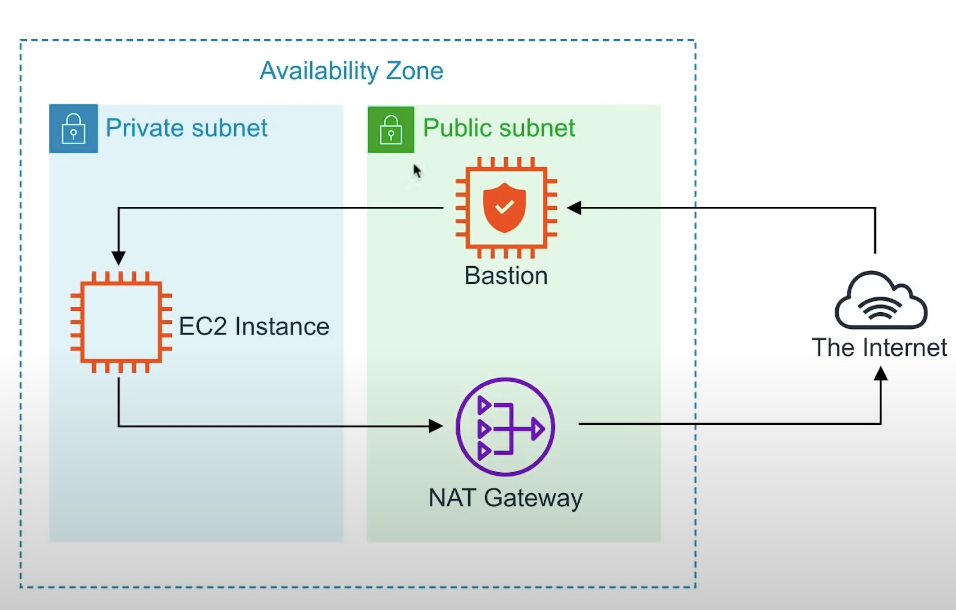
They are also known as jumpbox, beacuse you jump from one box to access another.
NATs cannot/should not be used as Bastions.
! Bastion could be replaced by session manager
AWS Direct Connect
establishing dedicated network connections from on-premises locations to AWS
very fast network Lower Bandwidth 50M-500M or Higher Bandwidth 1GB or 10GB
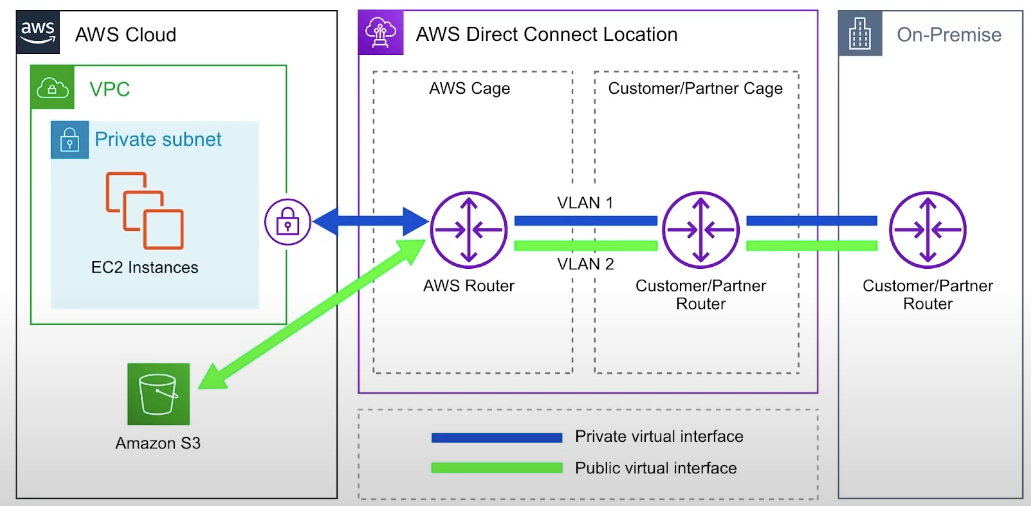
- helps reduce network costs and increase bandwidth throughput
- provides a more consistent network experience that a typeical internet-based connection
Dierct Connect Example
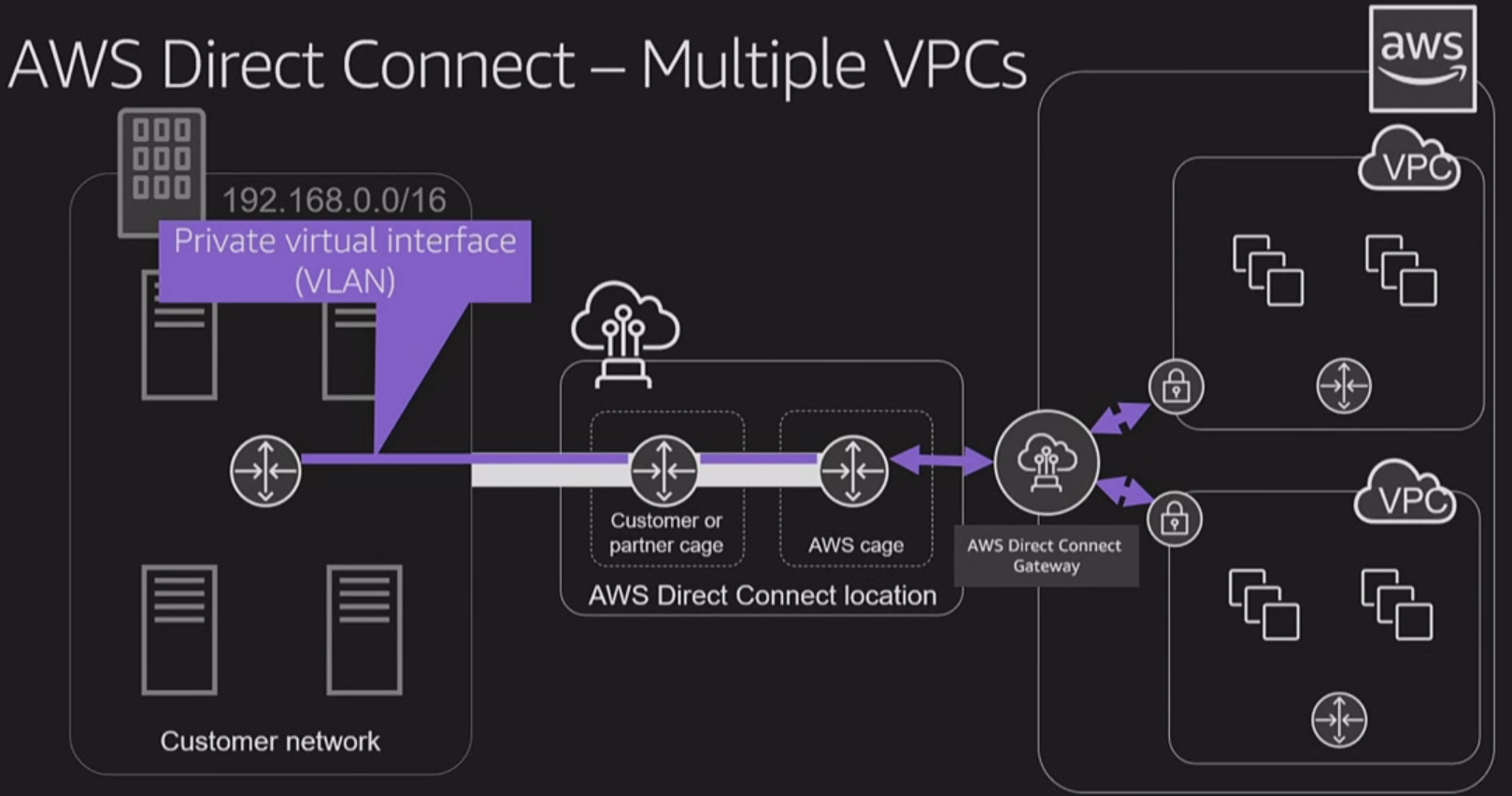
Diect Connect work with TGW
VPC Example
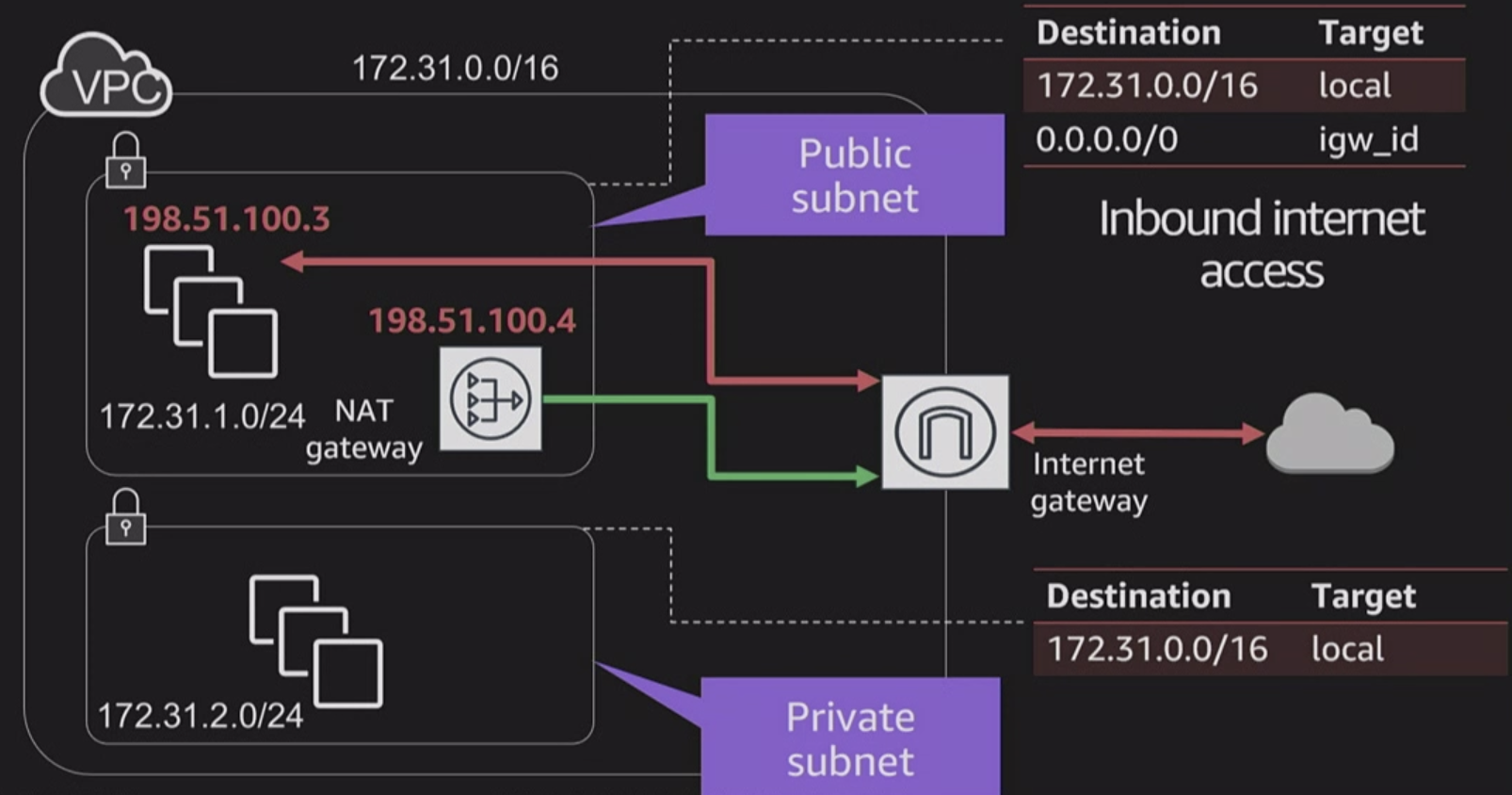
use NAT
NAR route rule: 0.0.0.0/0
inbound and outbound
VPC CheatSheet
Amazon VPC lets you provision a logically isolated section of the Amazon Web Services (AWS) cloud where you can launch AWS resources in a virtual network that you define.
Analogous to having your own DC inside AWS.
Provides complete control over the virtual networking environment including selection of IP ranges, creation of subnets, and configuration of route tables and gateways.
A VPC is logically isolated from other VPCs on AWS.
Possible to connect the corporate data centre to a VPC using a hardware VPN (site-to-site).
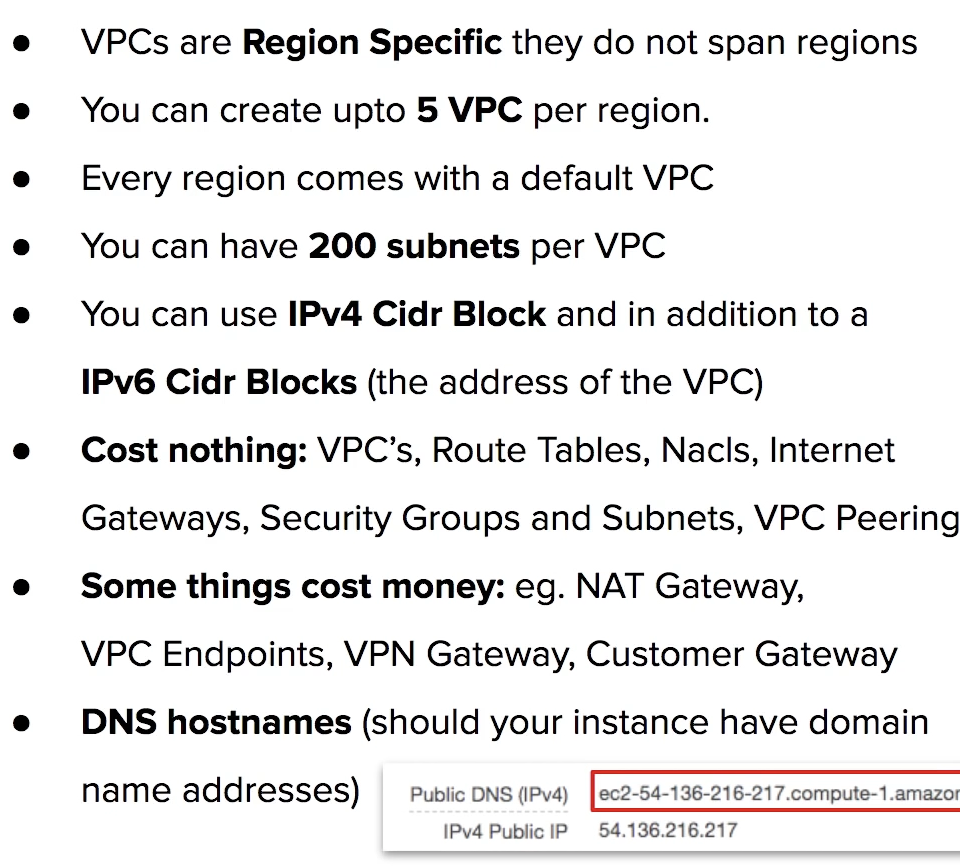
VPCs are region wide.
A default VPC is created in each region with a subnet in each AZ.
By default you can create up to 5 VPCs per region.
You can define dedicated tenancy for a VPC to ensure instances are launched on dedicated hardware (overrides the configuration specified at launch).
A default VPC is automatically created for each AWS account the first time Amazon EC2 resources are provisioned.
The default VPC has all-public subnets.
Public subnets are subnets that have:
- “Auto-assign public IPv4 address” set to “Yes”.
- The subnet route table has an attached Internet Gateway.
Instances in the default VPC always have both a public and private IP address.
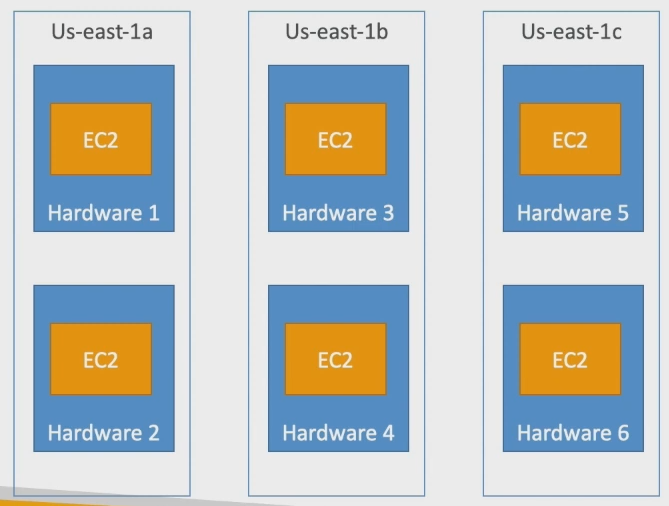
AZs names are mapped to different zones for different users (i.e. the AZ “ap-southeast-2a” may map to a different physical zone for a different user).
Components of a VPC:
- A Virtual Private Cloud: A logically isolated virtual network in the AWS cloud. You define a VPC’s IP address space from ranges you select.
- Subnet: A segment of a VPC’s IP address range where you can place groups of isolated resources (maps to an AZ, 1:1).
- Internet Gateway: The Amazon VPC side of a connection to the public Internet.
- NAT Gateway: A highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet.
- Hardware VPN Connection: A hardware-based VPN connection between your Amazon VPC and your datacenter, home network, or co-location facility.
- Virtual Private Gateway: The Amazon VPC side of a VPN connection.
- Customer Gateway: Your side of a VPN connection.
- Router: Routers interconnect subnets and direct traffic between Internet gateways, virtual private gateways, NAT gateways, and subnets.
- Peering Connection: A peering connection enables you to route traffic via private IP addresses between two peered VPCs.
- VPC Endpoints: Enables private connectivity to services hosted in AWS, from within your VPC without using an an Internet Gateway, VPN, Network Address Translation (NAT) devices, or firewall proxies.
- Egress-only Internet Gateway: A stateful gateway to provide egress only access for IPv6 traffic from the VPC to the Internet.
Options for connecting to a VPC are:
- Hardware based VPN.
- Direct Connect.
- VPN CloudHub.
- Software VPN.
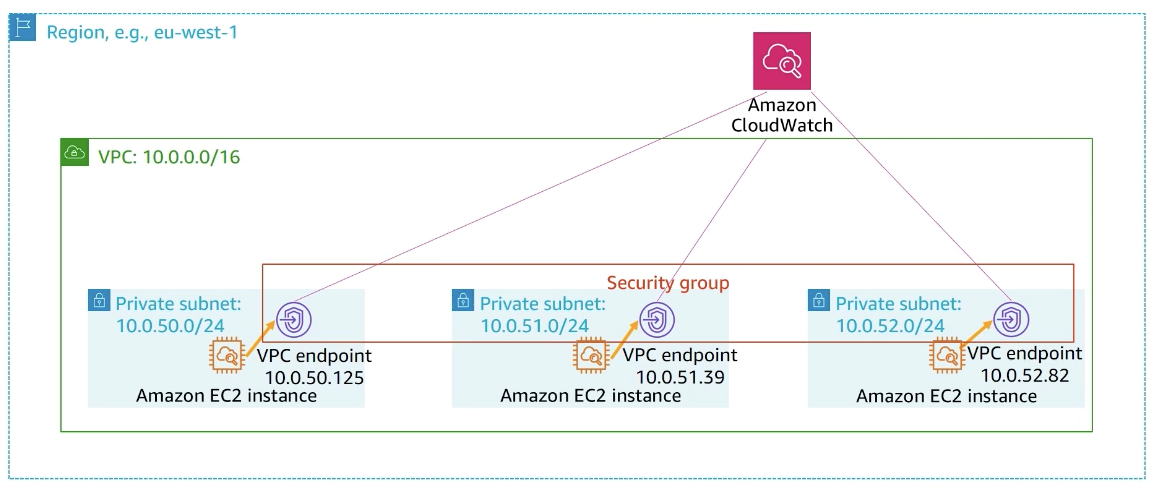
VPC Endpoints
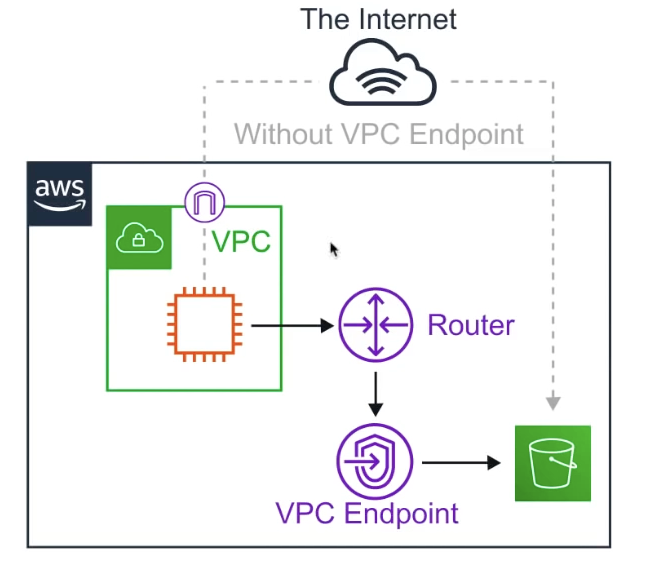
Allow you to privately connect your VPC to other AWS services, and VPC endpoint services.
- Eliminates the need for IGW, NAT, VPN or AWS Direct Connect
- Instances in the VPC do not require a pubic IP address to communicate with service resources
- Traffic between your VPC and other services does not leave the AWS network
- Horizontally scaled, redundant and highly available VPC component
- allows secure communication between instances and services - without adding availability risks or bandwidth contraints on your traffic
2 Types of VPC Endpoints:
Interface Endpoints
Elastic Network Interfaces (ENI) with a private IP address
serve as an entry point for traffic foing to a supported service
IE are powered by AWS PrivateLink (keep traffic within AWS network)
[Pricing]
Pricing per VPC endpoint per AZ 0.01 $/hour
Pricing per GB data processed 0.01$
~$7.5/month

Gateway Endpoints
Free
GE is a gateway that is a target for a specific route in your route table
- to create a gatewat endpoint, you must sepcify the VPC in which you want to create the endpoint, and the service to which you want to establish the connection
!!! Only supports 2 services (S3 and DynamoDB) !!!
VPC Endpoint CheatSheet

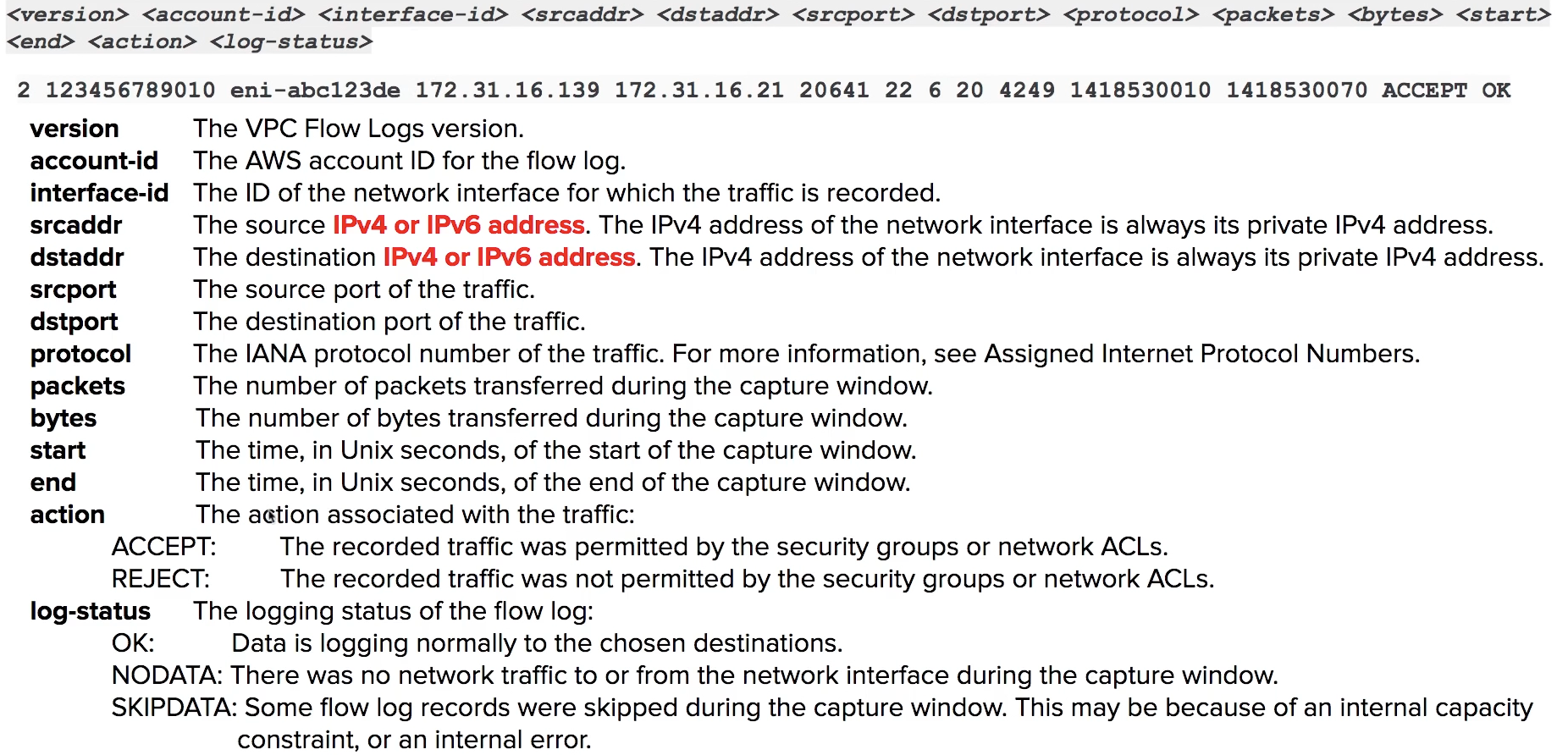
VPC Flow Logs
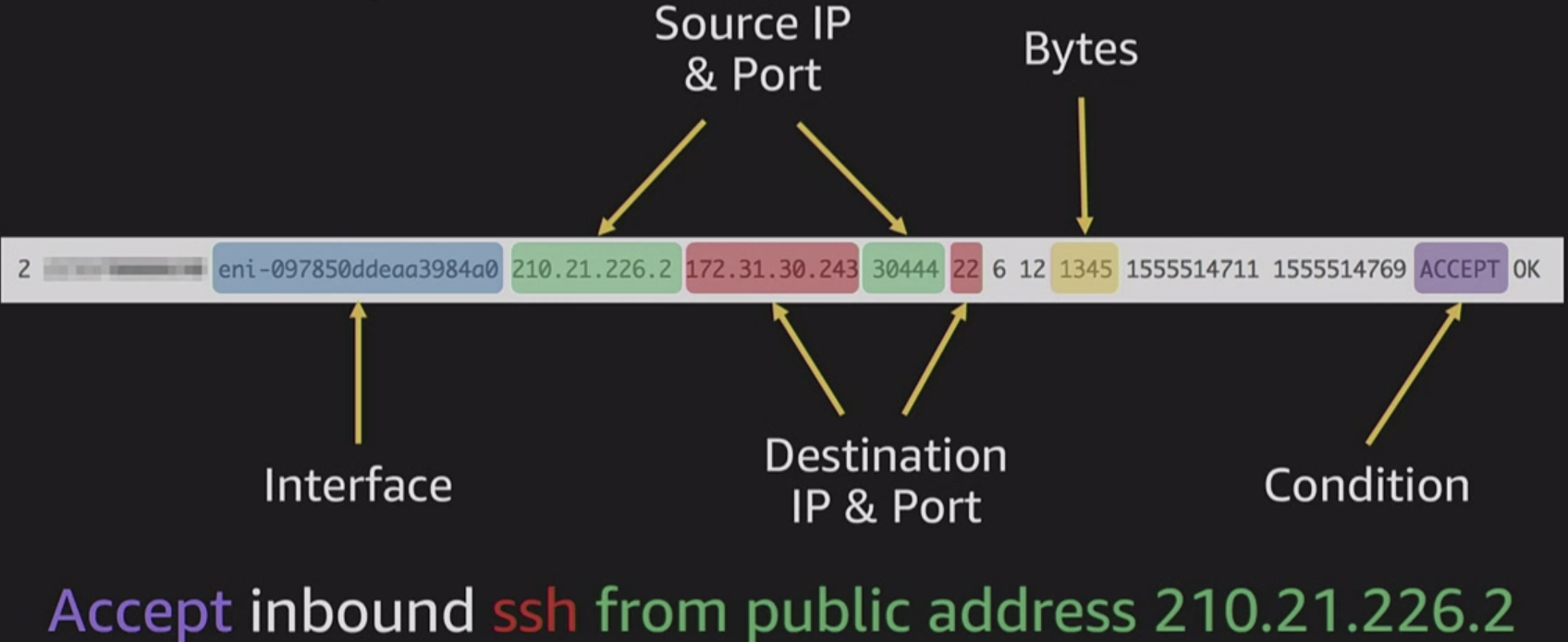
allow yout to capture IP traffic information in-and-out of Network Interfaces within your VPC
Three levels:
- VPC
- Subnets
- Network Interface
All log data is stored using Amazon CloudWatch Logs.
FLow Logs Breakdown
FL CheatSheet
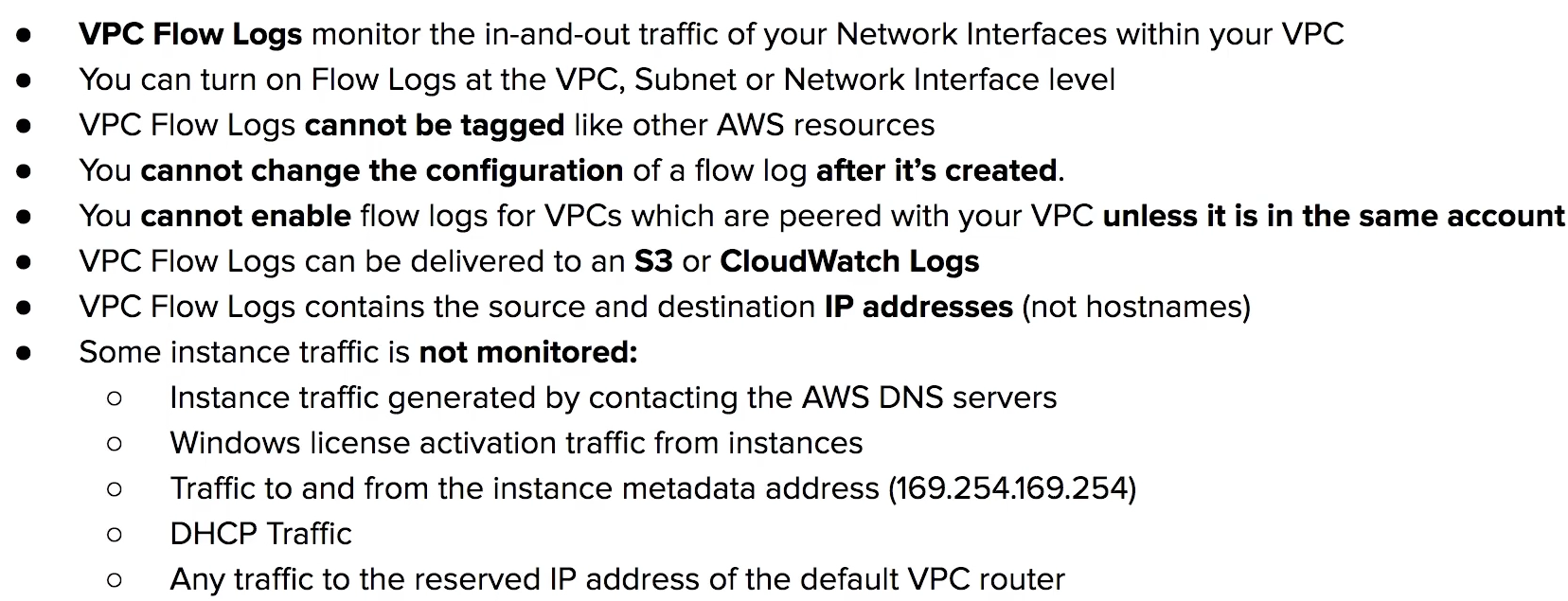
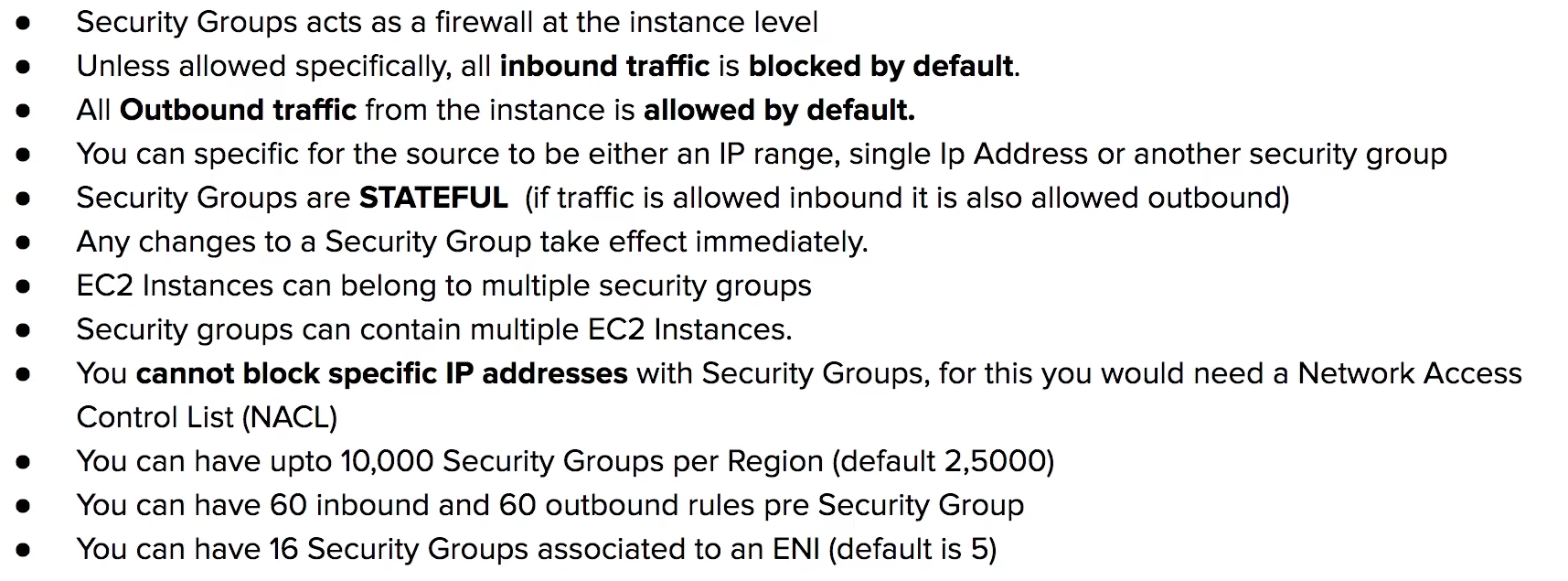
Network Access Control Lists (NACLs)
an optional layer of security that acts as a firewall for controlling traffic in and out of subnets
virtual firework at subnet level
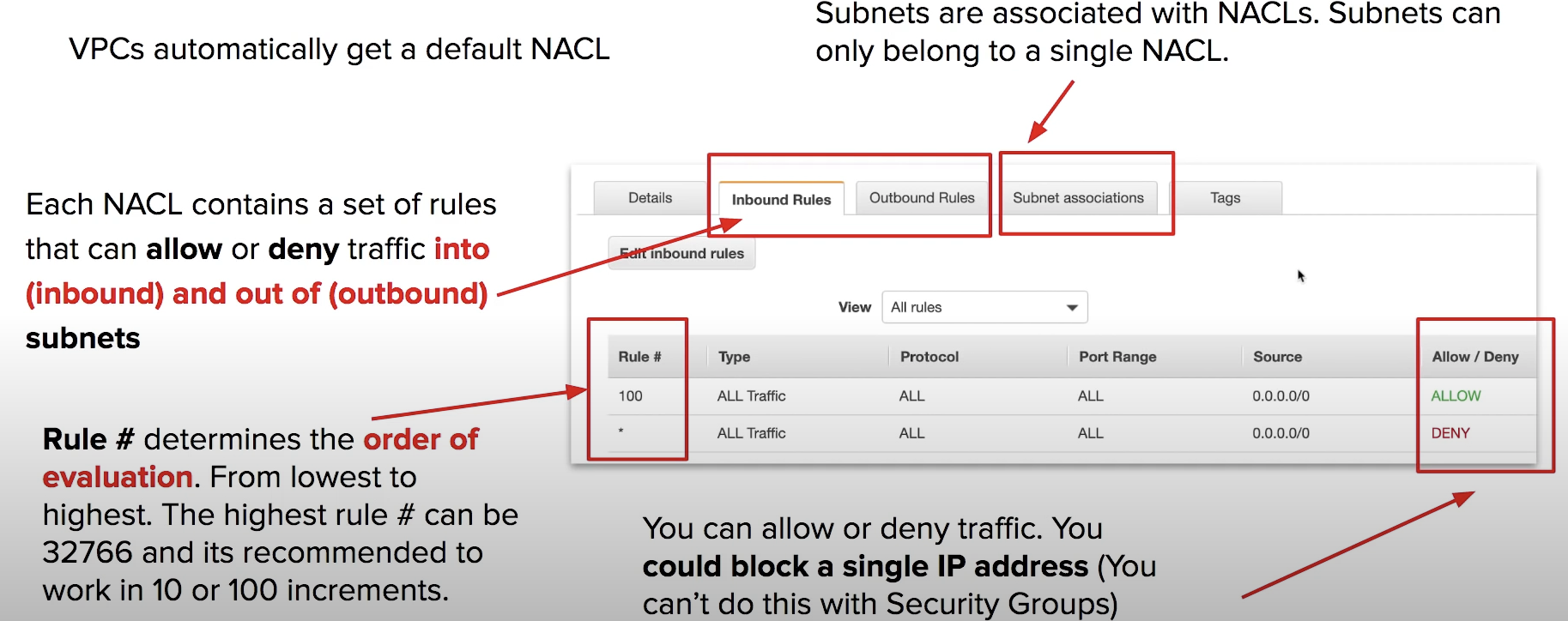
Example
suppose there is a malicious actor at a specific IP address is trying to access our instances so we block their IP
we never need to SSH into instances so we add a DENY for these subnets.
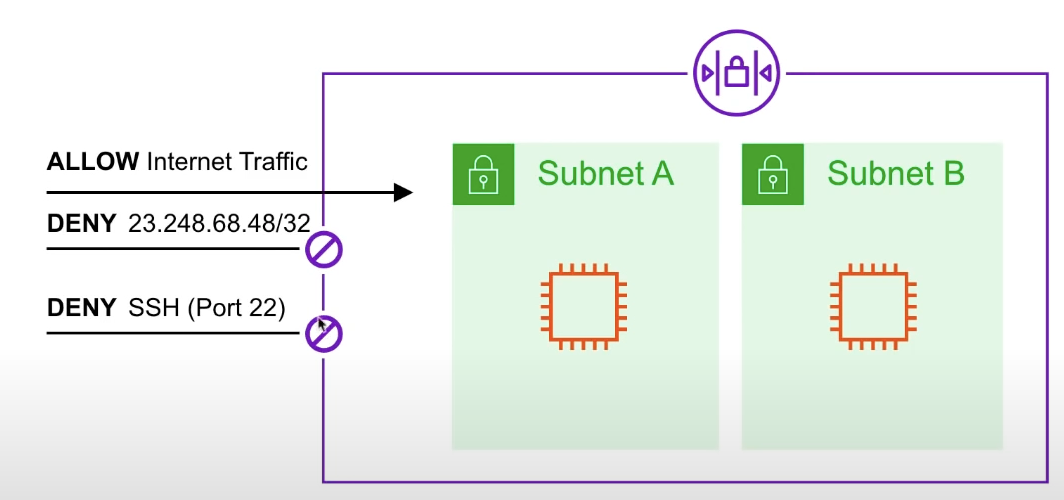
NACLs Cheat Sheet
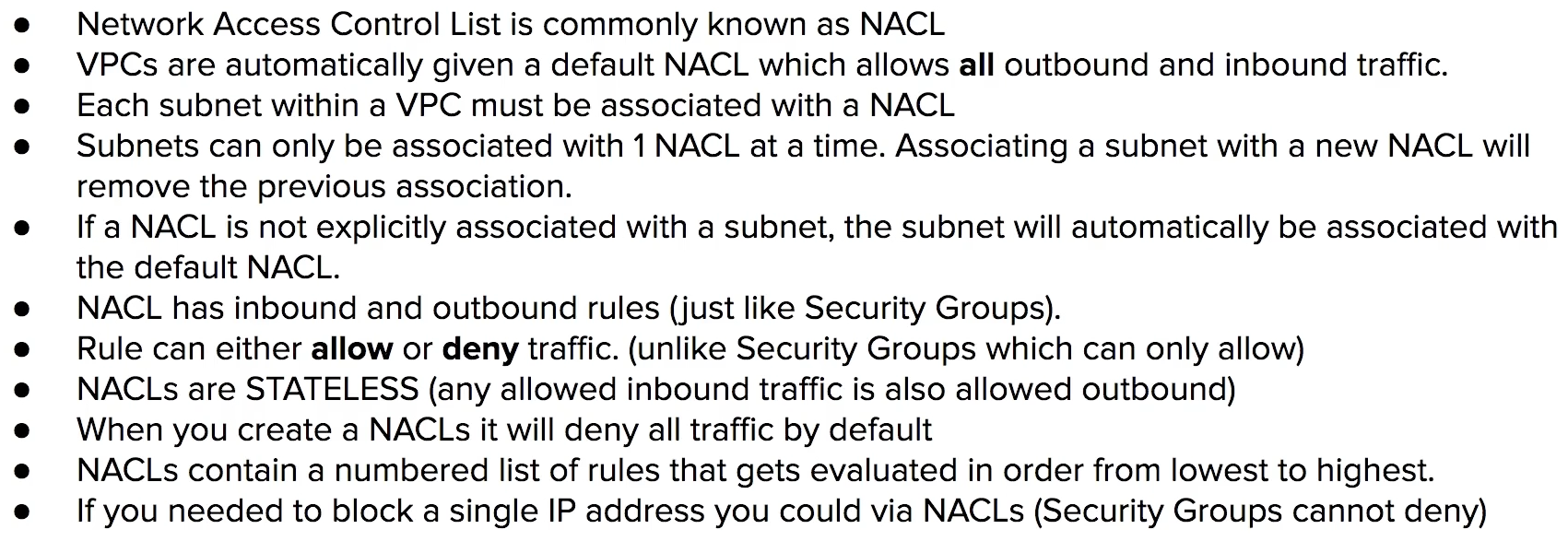
Security Group
virtual firewall at the instance level
security group are assocated with EC2 instances
Multiple Instances across multiple subnets can belong to a Security Group
Use Case
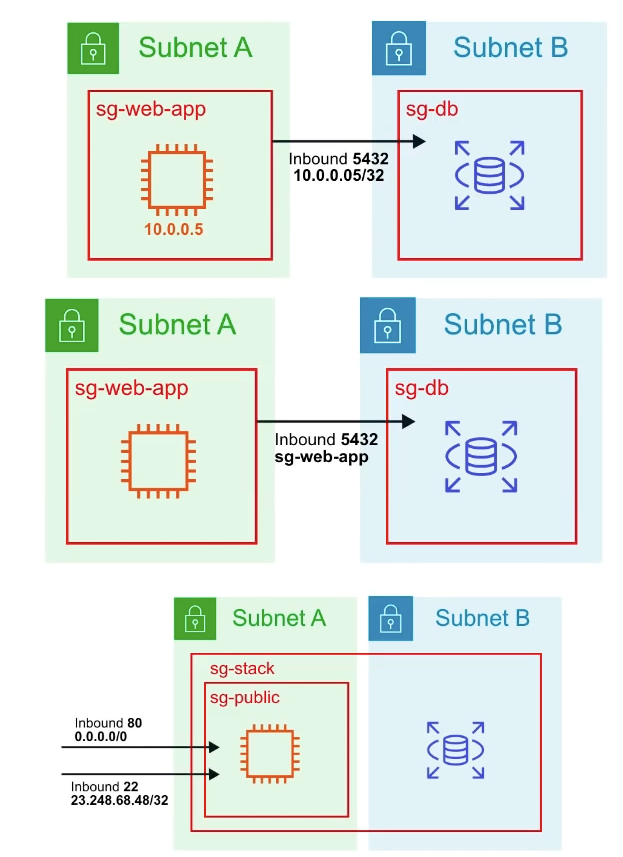
you can specify the source to be an IP address or a specific ip (/32 is and IP address)
you can sepcify the source to be another security group
An instance can belong to multiple security groups, and rules are permissive (instead of restrictive). One SG which has no Allow and you add an allow to another than it will allow.
SG Limits

SG CheatSheet
NACLs vs. SG vs. WAF
- WAF
api gateway (non-private)
cloudfront distributions
load balancers (where you want additional rules/checks such as OWASP, cross-site-scripting etc)
- NACL
whitelisting specific IP’s/CIDR’s to a subnet, i.e. allowing only application tier subnet(s) to access database tier subnet(s).
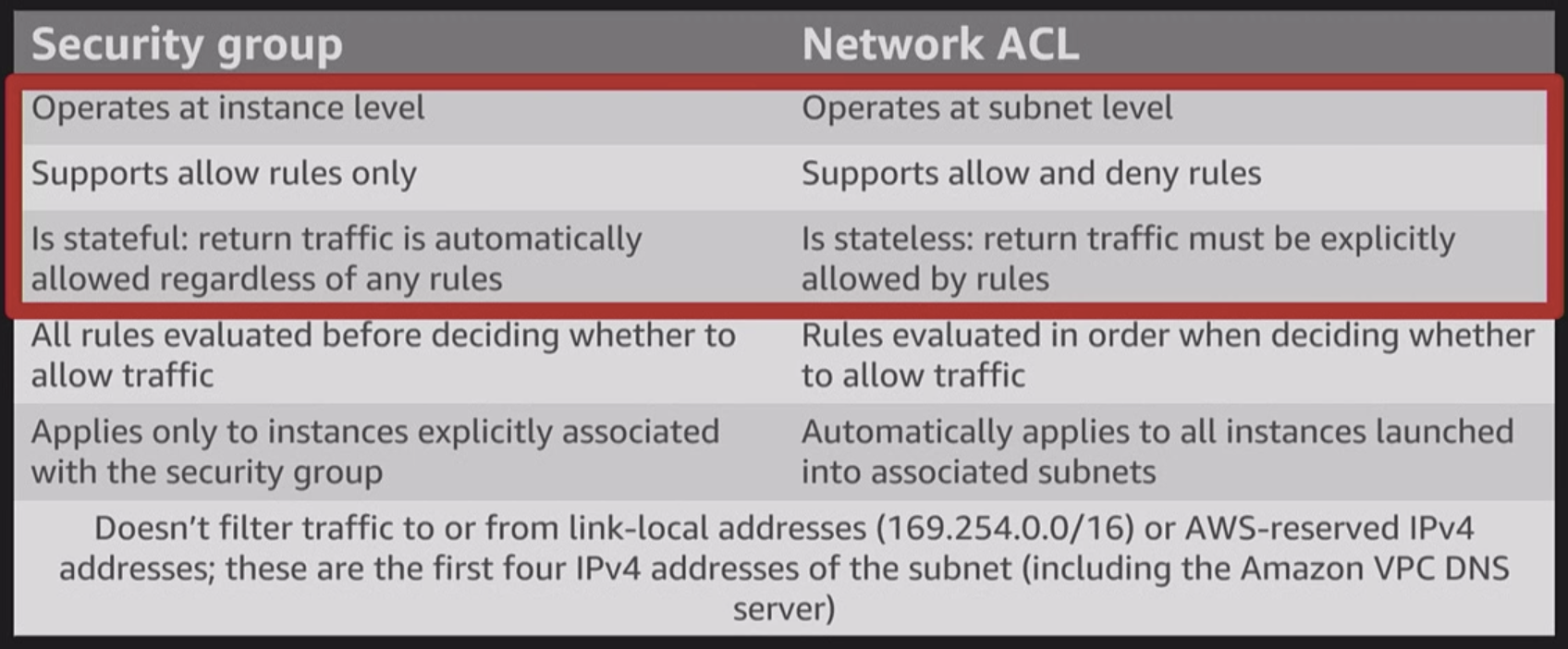
WAF
Web Application Firewall (WAF)
WAF ACL
AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits and bots that may affect availability, compromise security, or consume excessive resources.
AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that control bot traffic and block common attack patterns, such as SQL injection or cross-site scripting.
Rules
predefined and customer
You can also customize rules that filter out specific traffic patterns. You can get started quickly using Managed Rules for AWS WAF, a pre-configured set of rules managed by AWS or AWS Marketplace Sellers to address issues like the OWASP Top 10 security risks and automated bots that consume excess resources, skew metrics, or can cause downtime. These rules are regularly updated as new issues emerge. AWS WAF includes a full-featured API that you can use to automate the creation, deployment, and maintenance of security rules.
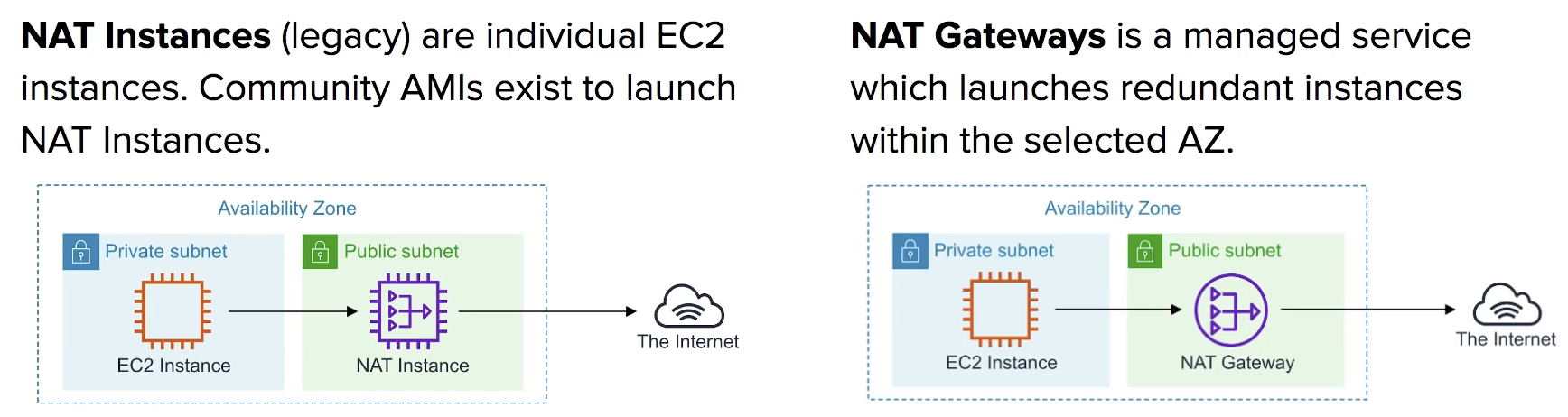
NAT
Networl Address Translation
method of remapping one IP address space into another
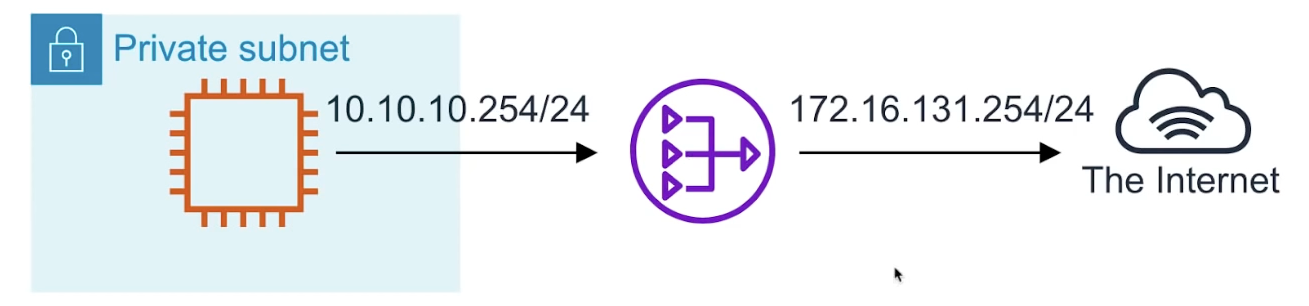
If you have a private network and need to help gain outbound access to the Internet you would need to use a NAT gateway to remap the Private IPs.
If you have two networks which have conflicting network address you can use a NAT to make the addresses more agreeable.
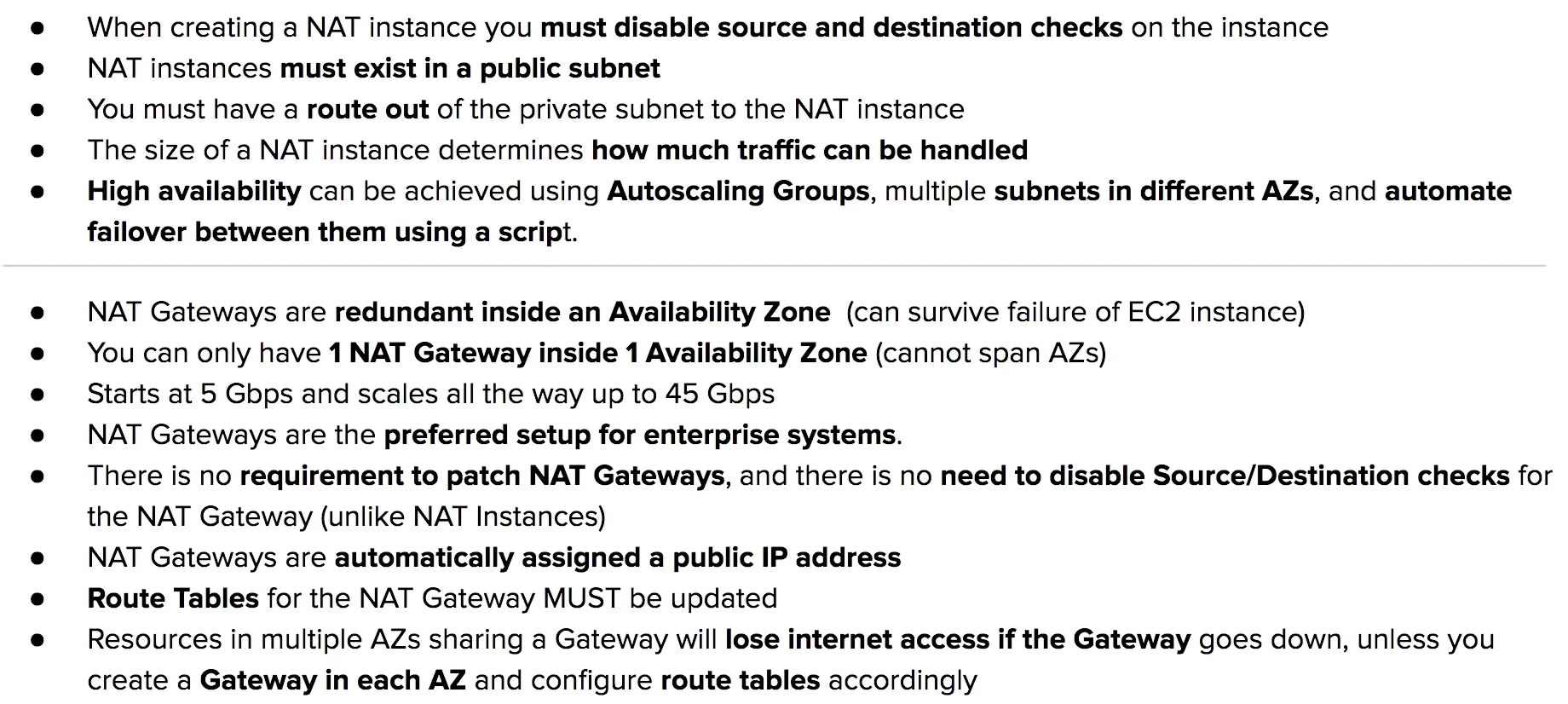
NAT Instances vs. NAT Gateway
NATs have to run with Public Subnet
NAT Cheat Sheet
IAM
Identity Access Management
manage access of AWS users and resources
IAM Core Componets
- IAM Users
End users who log into the console or interact with AWS resource programmatically
- IAM Groups
Group up your Users so they all share permission levels of the group
ex. Administrators, Developers, Auditors
- IAM Roles
Associate permissions to a Role and then assign this to an Users or Groups
- IAM Policies
JSON documents which grant permissions for a specific user, group or role to access service. Policies are attached to IAM identities
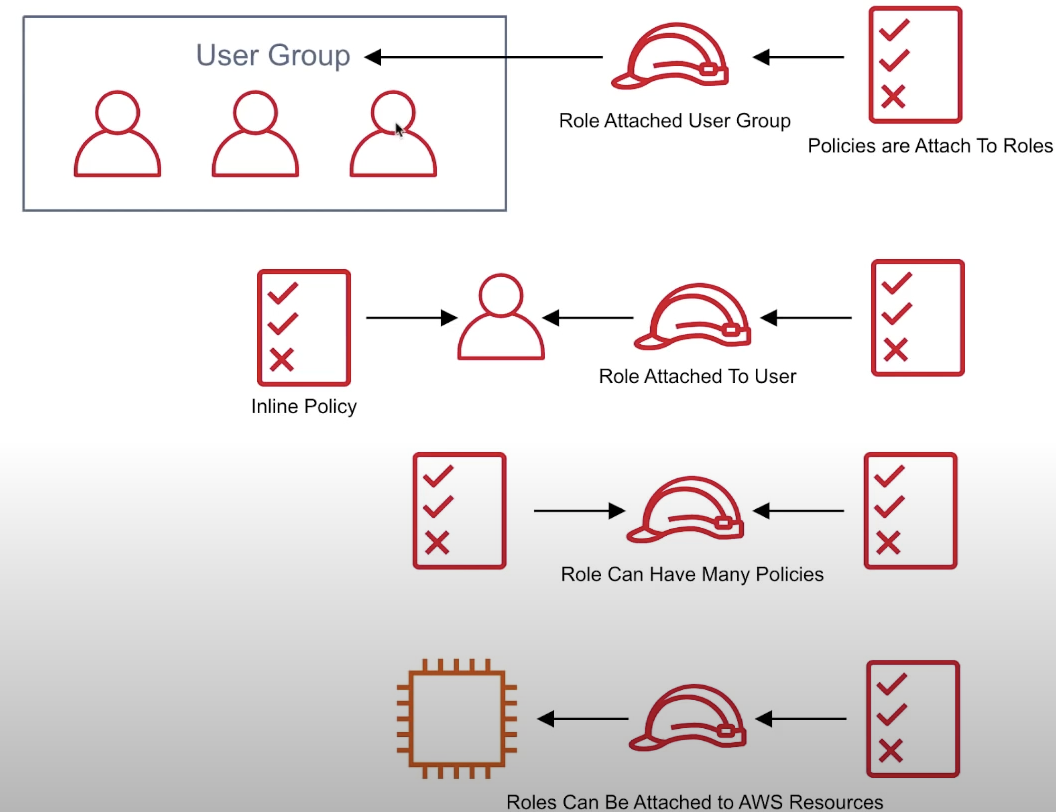
A user can belong to a group, roles can be applied to groups
A user can have a role directly attached, a policy can be directly attached to a user (inline policy)
Roles can have many policeies attached
Various AWS resources allow you attach roles directly to them
Types of Policies
- Managed Policies
a policy which is managed bu AWS, which you can not edit. Manahed policies are labeld with an orange box
- Customer Managed Policies
a policy created by the customer which is editable. Customer policies have no symnol beside them
- Inline Policies
a policy which is directly attached to the user
Policy Structure
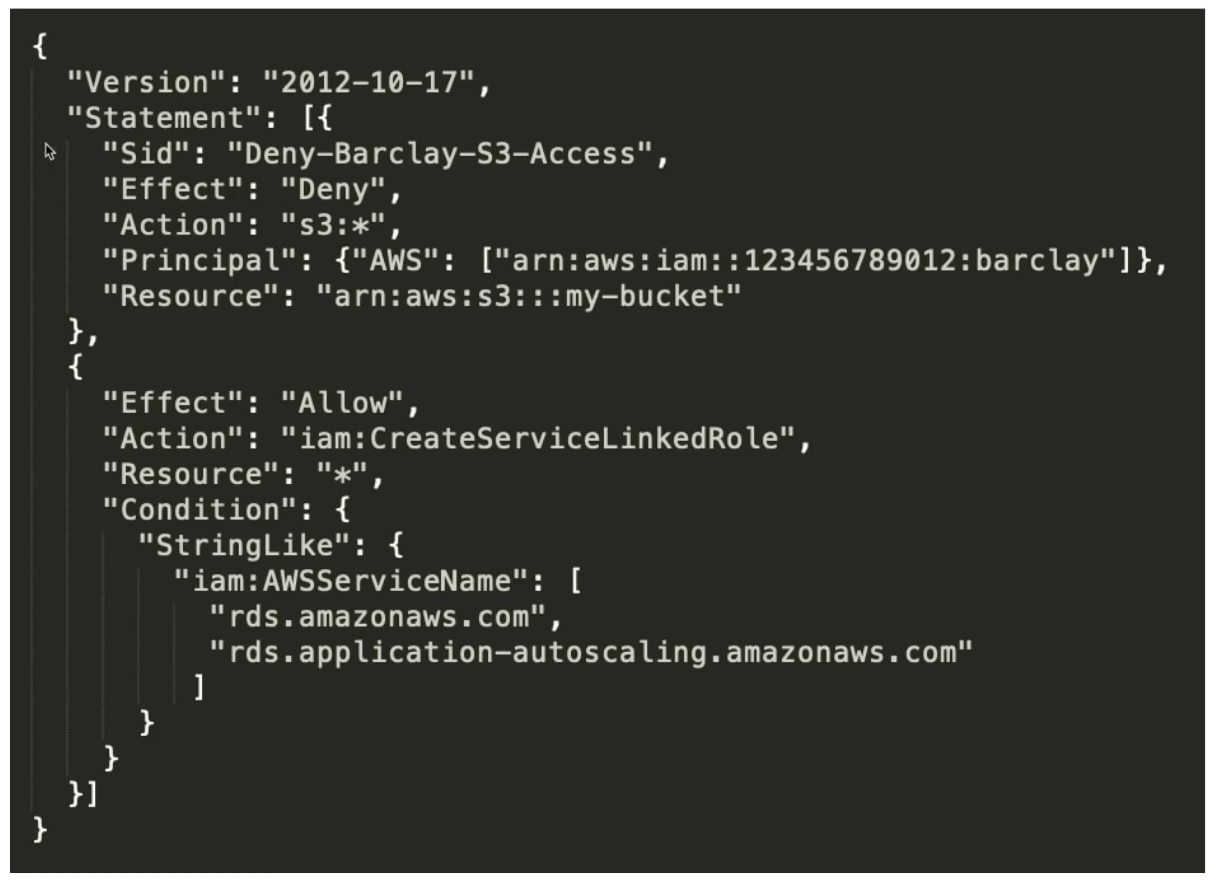
Version:
Statement: container for the policy element, you are allowed to have multiples
Sid (Optional)
Effect: allow or deny
Principal: account, user, role or federated user
Action: list or actions that the policy allows or denies
Resource: the resources to which the actions applies
Condition (optional): circumstances
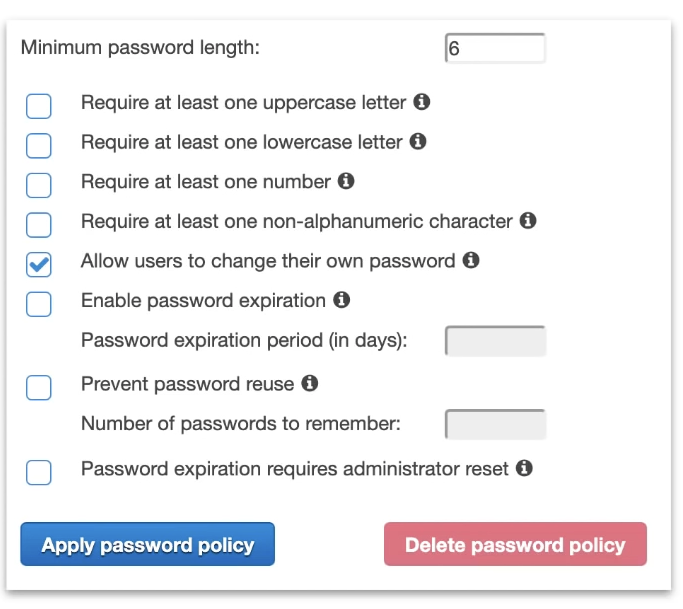
Password Policy (User)
In IAM you can set a Password Policy to set minimum requirements of a password and rotate passwards so users have to update their password periodically.
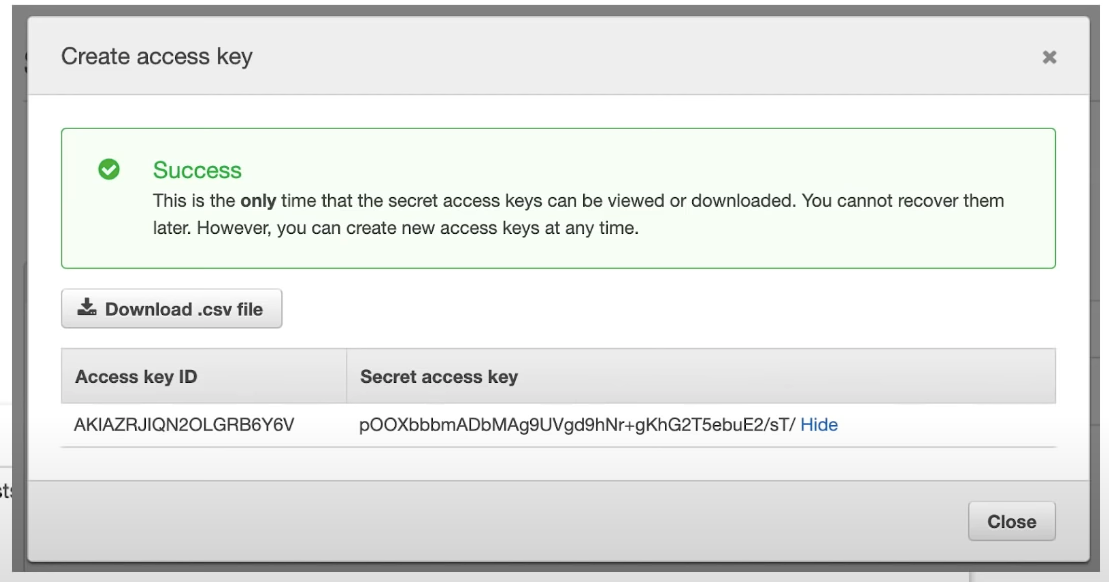
Access Keys
allow users to interact with AWS service programmatically via the AWS CLI or AWS SDK
you are allowed two access key per user
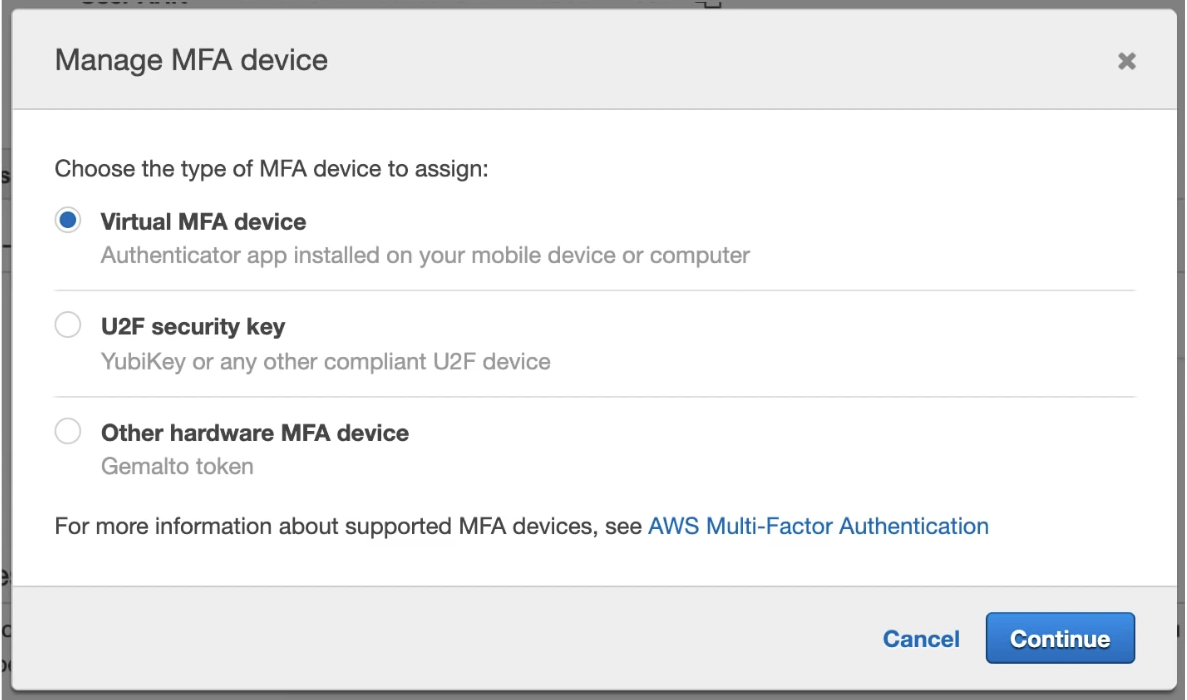
MFA
multiple factor authentication
can be turned on per user
user can turn on MFA, and root user can enforce users to have MFA
admin account could create policy requiring MFA to access certain resources
IAM CheatSheet
!!!Free Service!!!
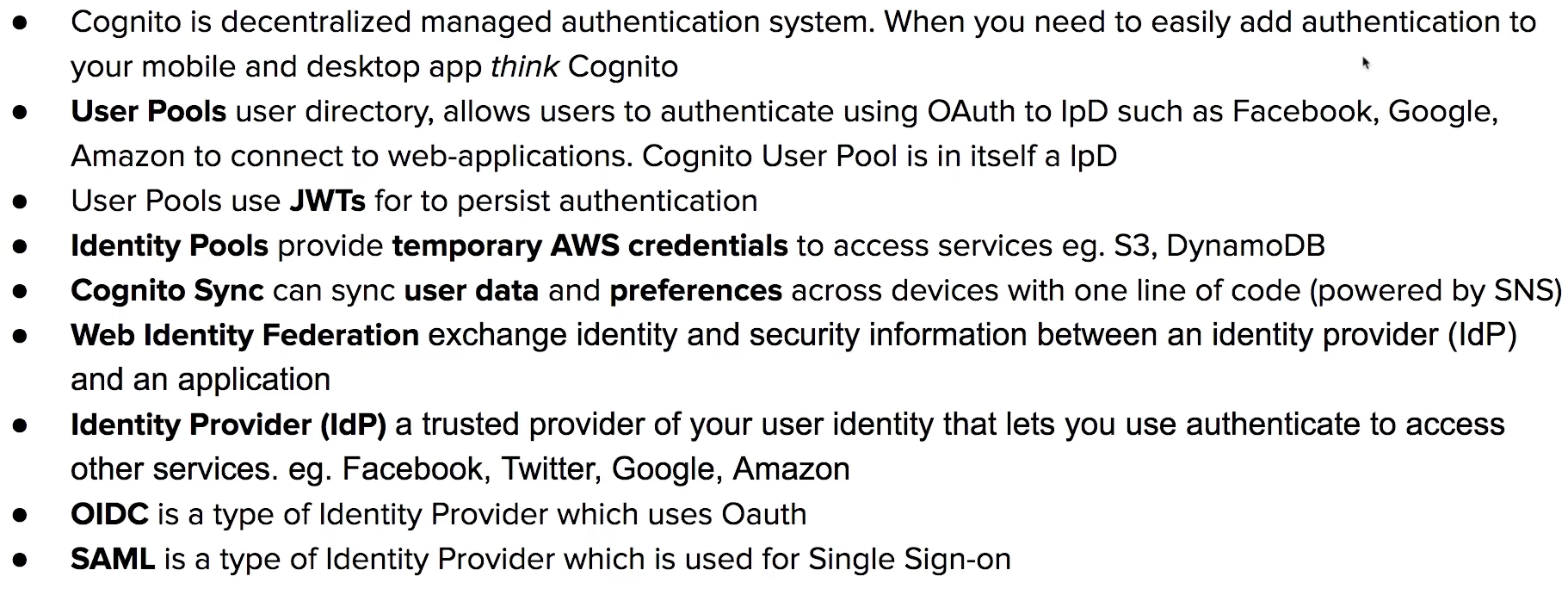
Cognito
decentrailzed managed authentication.
sign-up, sign-in integration for your apps.
socail identity provider eg. FB, Google
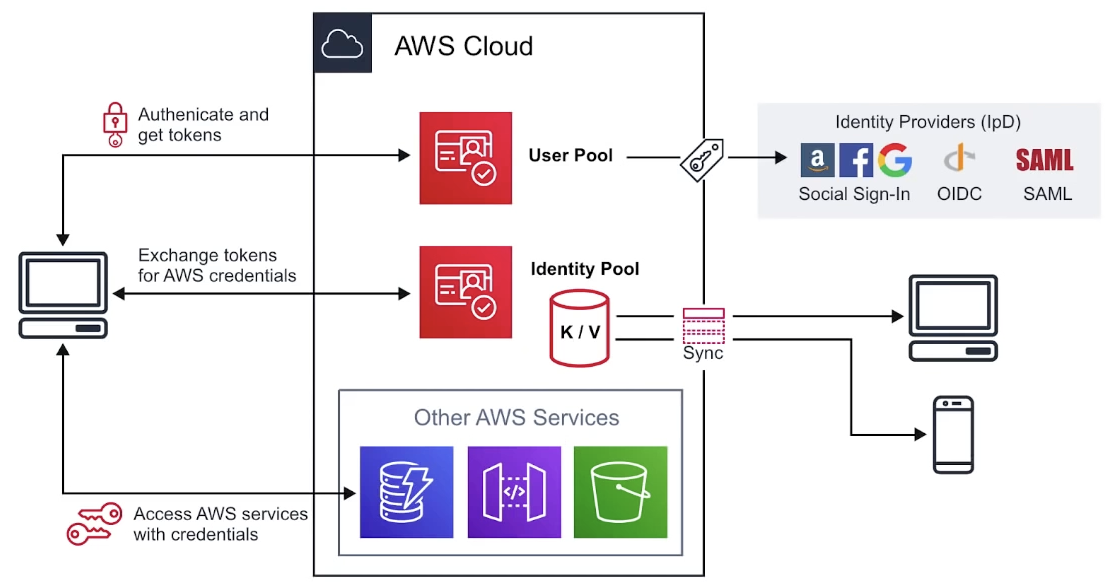
Web Identity Federation
WIF
to exchange identity and security information between an identity provider (IdP) and an application
Identity Provider (IdP)
a trusted provider of your user identity that lets you use authenticate to access other services.
like: FB, Amazon, Google, Twitter, Github or LinkedIn
Types of Identity Providers
he technology that behind the identity providers
- Security Assertion Markup Language (SAML)
- Signle Sign On (SSO)
- OpenID Connect (OIDC) OAuth
User Pools
user directory with auth to IpD to grant access to your app
- sign-up
- sign-in
- account recovery
- account confirmation
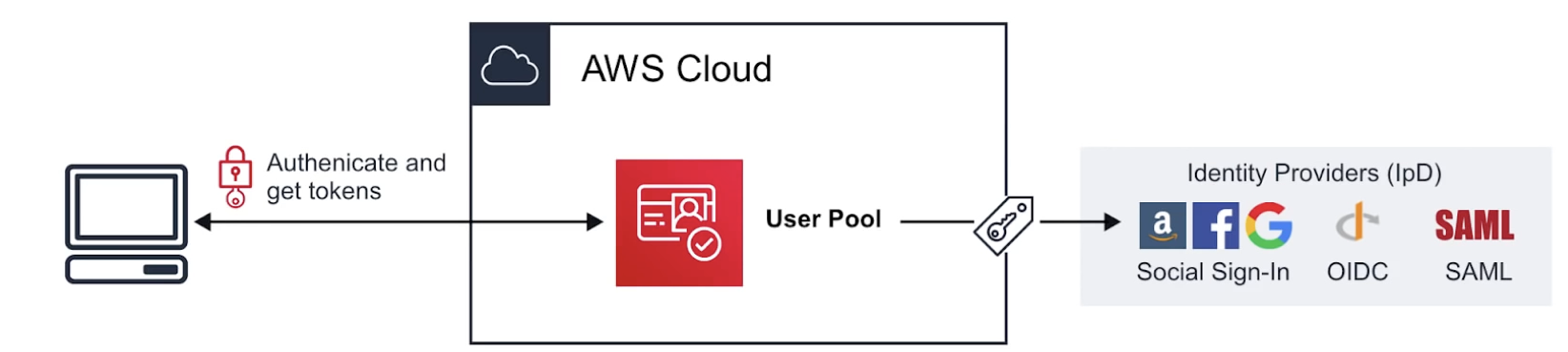
allows user to sign-in directly to UP, or using web identity federation
AWS Congito as the identity broker between AWS and the identity provider
sucessful user auth generates JWTs
UP can be thought of as the account used to access the system
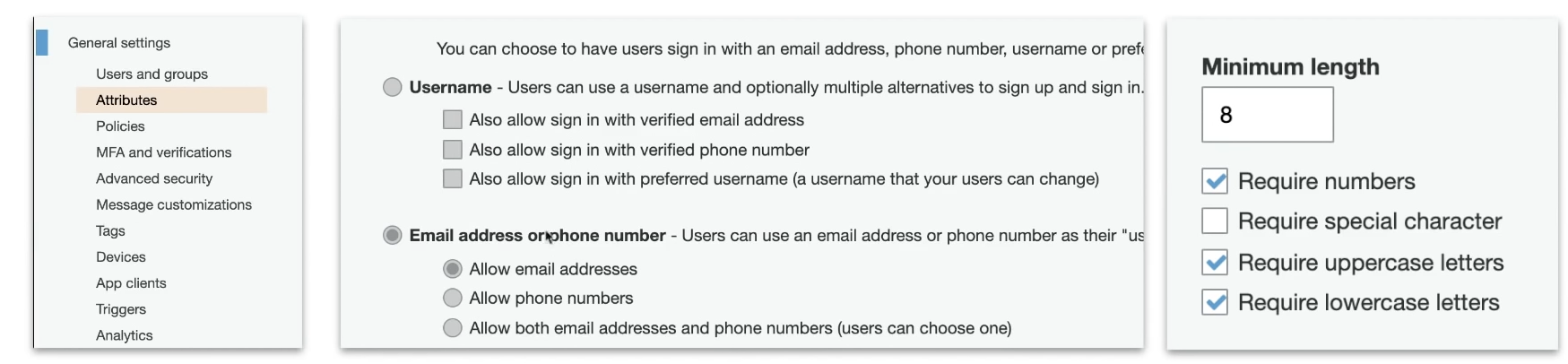
functions:
- choose what attributes
- choose password requirements
- apply MFA
- restrict whether users are allowed to sign up their own or need admin verification
- analytics with PinPoint for user campaigns
- trigger custom log via Lambdas after actions such as after signup
Identity Pools
provide temporary credentials for users to access AWS services, eg. S3, DynamoDB
tmp AWS credentials
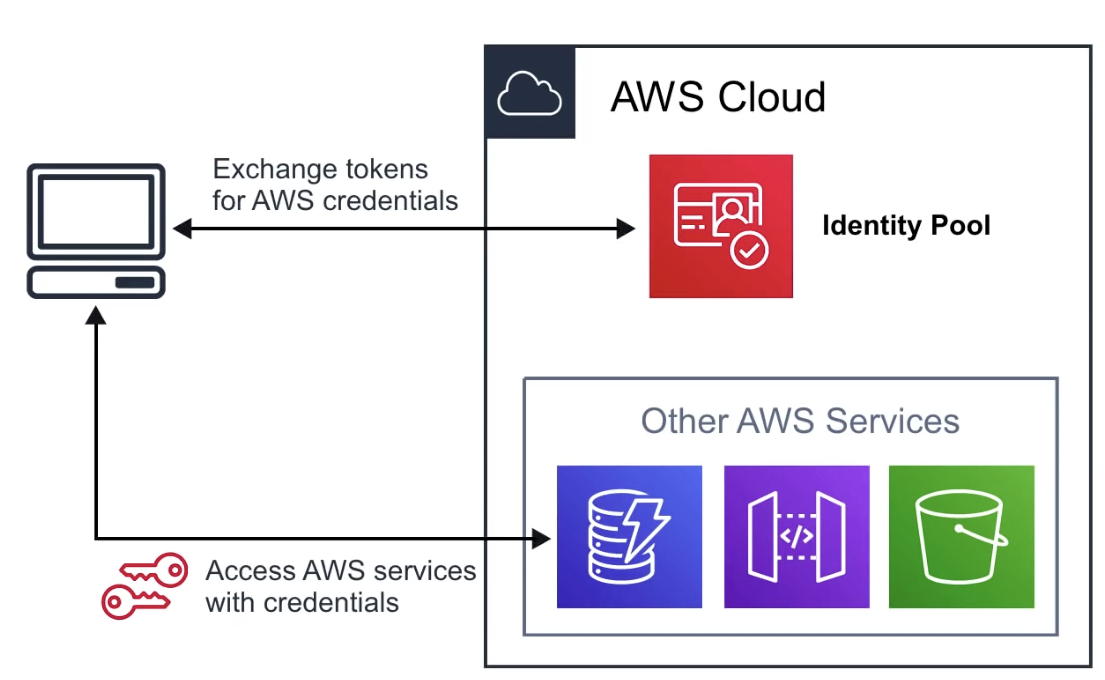
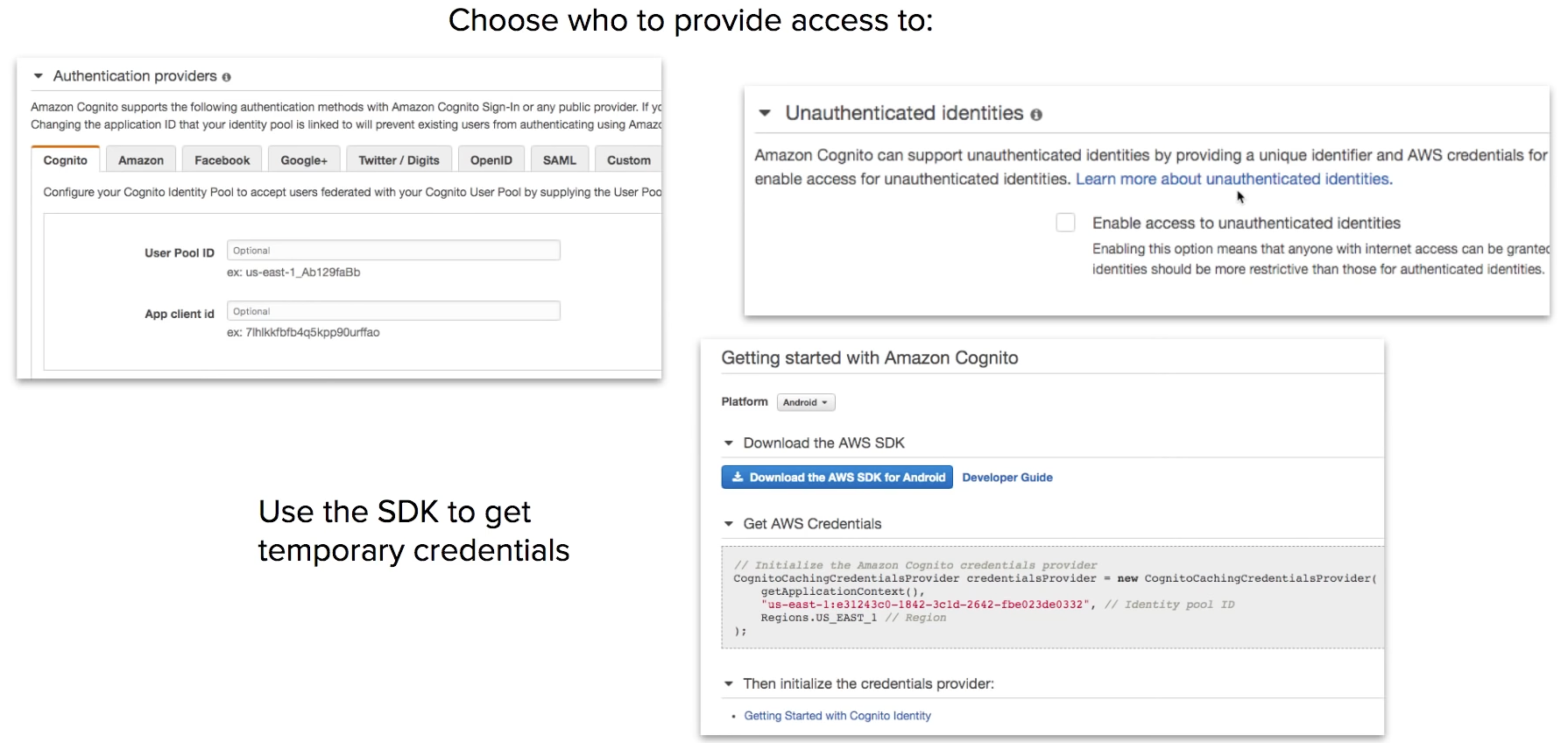
Sync
syncs user data and preferences across all devices with one line of code
cognito uses push synchronization to push updates and synchronize data uses SNS to send notifications to all user devices when data in the cloud changes
Cognito CheatSheet
AWS Security
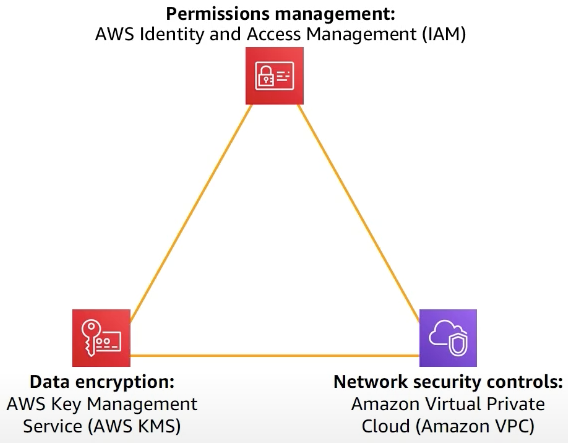
- Control your cloud infrastructure: AWS IAM
- Control your data: AWS KMS
- Control your network: Amazon VPC
IAM
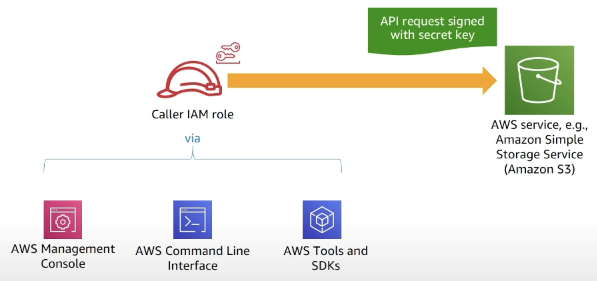
Every AWS service uses IAM to authenticate and authorize API calls
- for human callers:
IAM users
federated identities
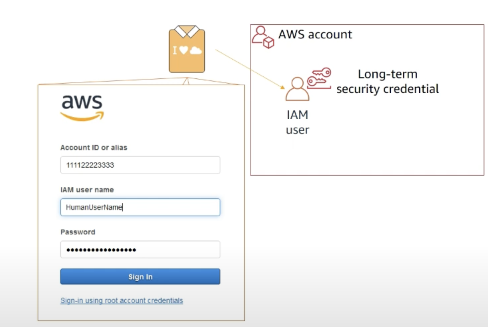
- for non-human callers

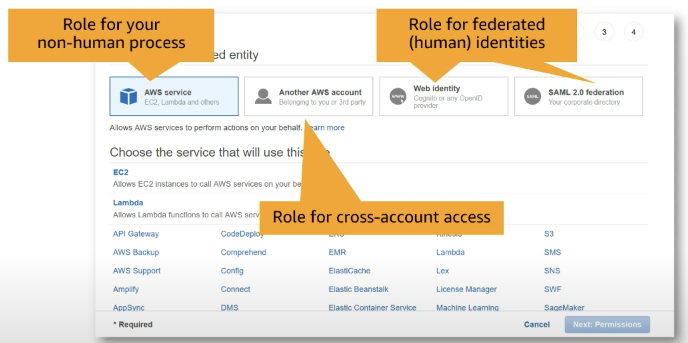
creating a role in the AWS management console
How an authentication works in AWS
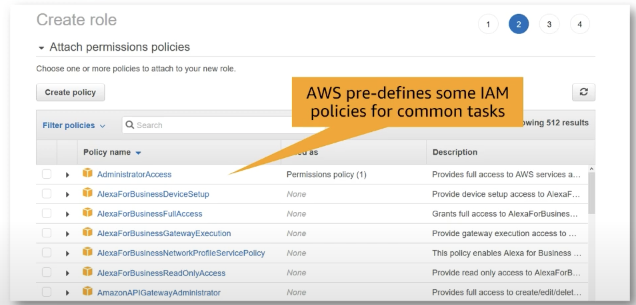
AWS-managed policies for common sets of permissions
orange box
cross-account auth → managing multi-account environments with AWS organizations
KMS
key management service
AWS-managed encryption and decryption service

For encrypting data, use envelope encryption
- KMS.GenerateDataKey → symmetric data key (plaintext and encrypted)
- Use plaintext data key to encrypt your data, then discard
- Store encrypted data key alongside your data
- To decrypted
- KMS.Decrypt(encryptedDataKey) → plaintextDataKey
- Then decrypt the data with the plaintext symmetric key
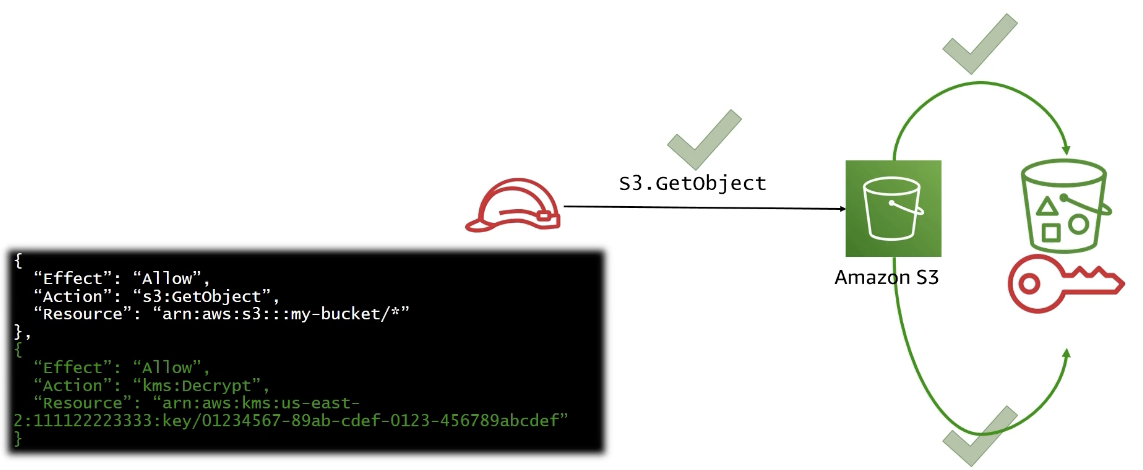
ex. KMS with S3
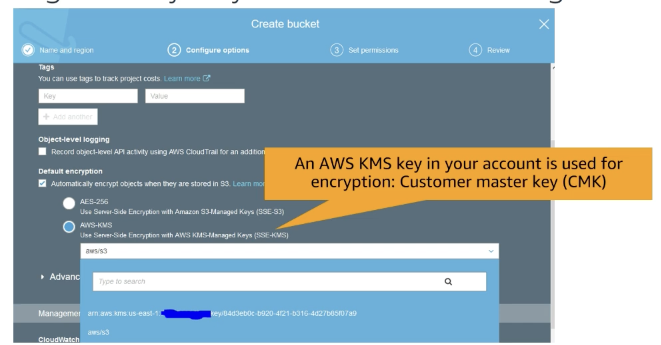
IAM permissions for AWS KMS key
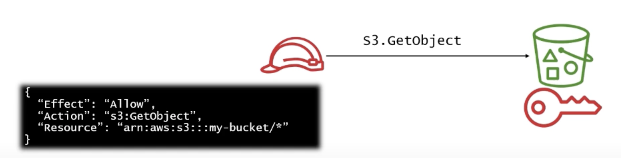
won’t work
VPC
network
VPC provides connectivity to and from that infrastructure
What builders need to know?
- VPC core concepts: subnets and security groups
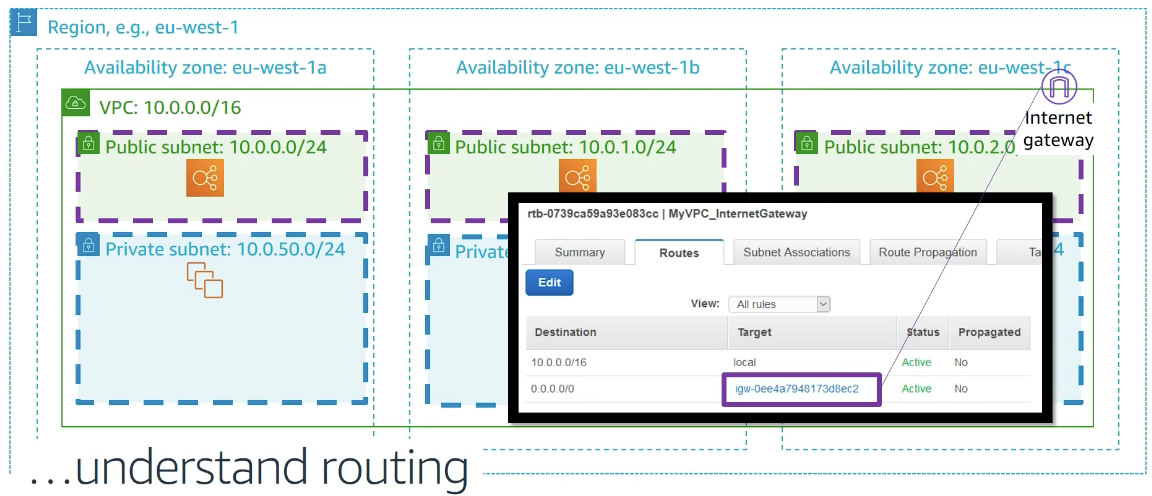
- routing basics
- private connectivity capabilities
subnets
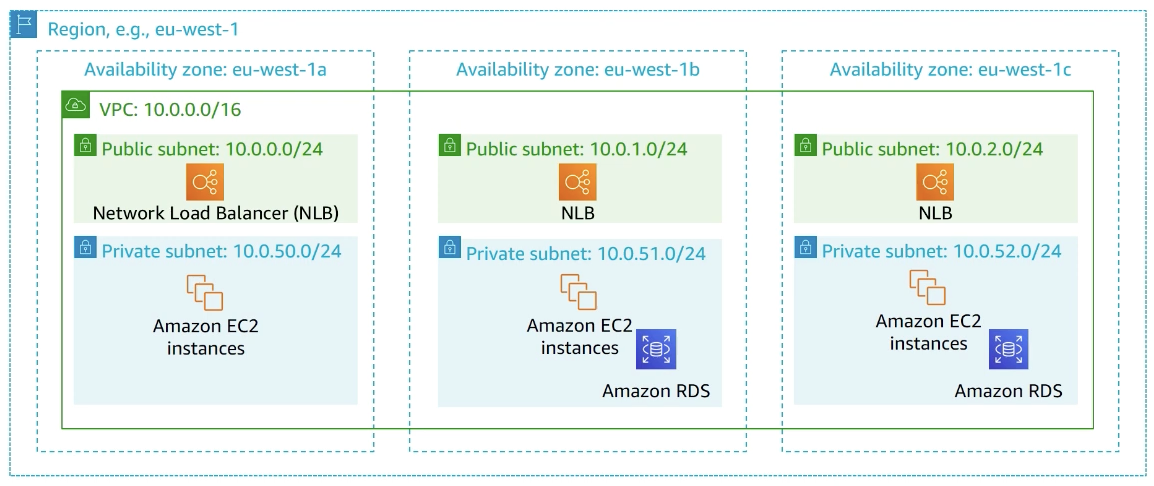
security group
like firewall
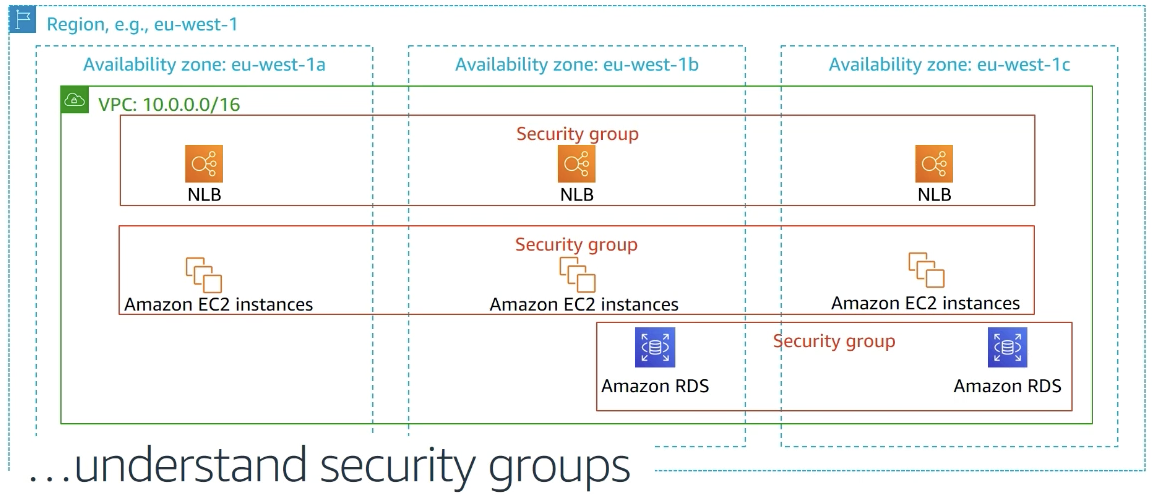
inbound rules, outbound rules
IGW
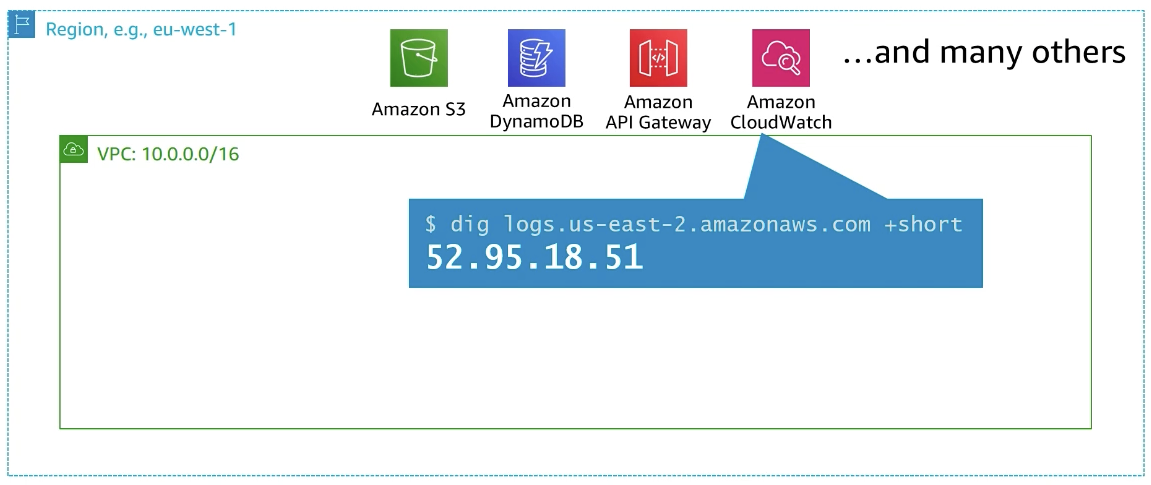
AWS resources not in your VPC
endpoints!
Placement Group
When you launch a new EC2 instance, the EC2 service attempts to place the instance in such a way that all of your instances are spread out across underlying hardware to minimize correlated failures. You can use placement groups to influence the placement of a group of interdependent instances to meet the needs of your workload. Depending on the type of workload, you can create a placement group using one of the following placement strategies:
Three Types (from small to large):
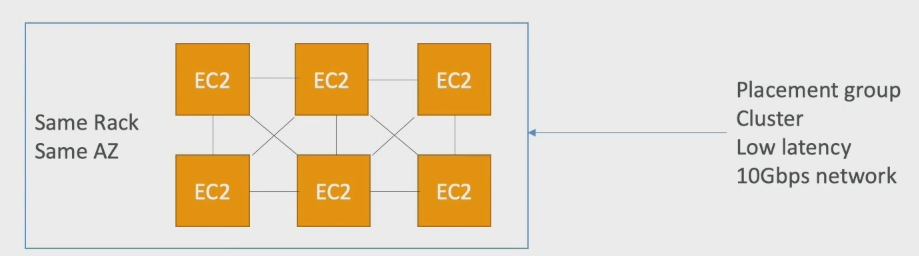
Cluster
packs instances close together inside an Availability Zone. This strategy enables workloads to achieve the low-latency network performance necessary for tightly-coupled node-to-node communication that is typical of HPC applications.
A cluster placement group can span peered VPCs in the same Region.
high-performance, high-risk
on same rack

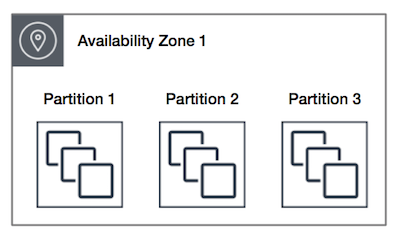
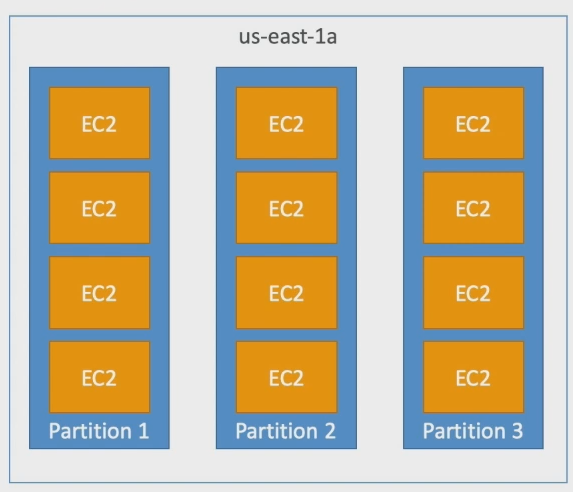
Partition (new)
spreads your instances across logical partitions such that groups of instances in one partition do not share the underlying hardware with groups of instances in different partitions. This strategy is typically used by large distributed and replicated workloads, such as Hadoop, Cassandra, and Kafka.
Amazon EC2 ensures that each partition within a placement group has its own set of racks.
partition are set of racks
up to 100+ instances per group
Spread
strictly places a small group of instances across distinct underlying hardware to reduce correlated failures.
on distinct rack, each rack having its own network and power source
max 7 instances per AZ per group